{"value":"Many developers today seek to improve productivity by finding better ways to collaborate, enhance code quality and automate repetitive tasks. We hear from some of our customers that they would like to leverage services such as Amazon Web Services CloudFormation, Amazon Web Services CodeBuild and other [Amazon Web Services Developer Tools](https://aws.amazon.com/products/developer-tools/) to manage their Amazon Web Services resources while continuing to use their existing CI/CD pipelines which they are familiar with. These services range from popular open-source solutions, such as Jenkins, to paid commercial solutions, such as Azure DevOps Server (formerly Team Foundation Server (TFS)).\n\nIn this post, I will walk you through an example to leverage the [Amazon Web Services Toolkit for Azure DevOps](https://aws.amazon.com/vsts/) to deploy your Infrastructure as Code templates, i.e. Amazon Web Services CloudFormation stacks, directly from your existing Azure DevOps build pipelines.\n\nThe Amazon Web Services Toolkit for Azure DevOps is a free-to-use extension for hosted and on-premises Microsoft Azure DevOps that makes it easy to manage and deploy applications using Amazon Web Services. It integrates with many Amazon Web Services services, including Amazon S3, Amazon Web Services CodeDeploy, Amazon Web Services Lambda, Amazon Web Services CloudFormation, Amazon SQS and others. It can also run commands using the Amazon Web Services Tools for Windows PowerShell module as well as the Amazon Web Services CLI.\n\n#### **Solution Overview**\n\nThe solution described in this post consists of leveraging the Amazon Web Services Toolkit for Azure DevOps to manage resources on Amazon Web Services via Infrastructure as Code templates with Amazon Web Services CloudFormation:\n\n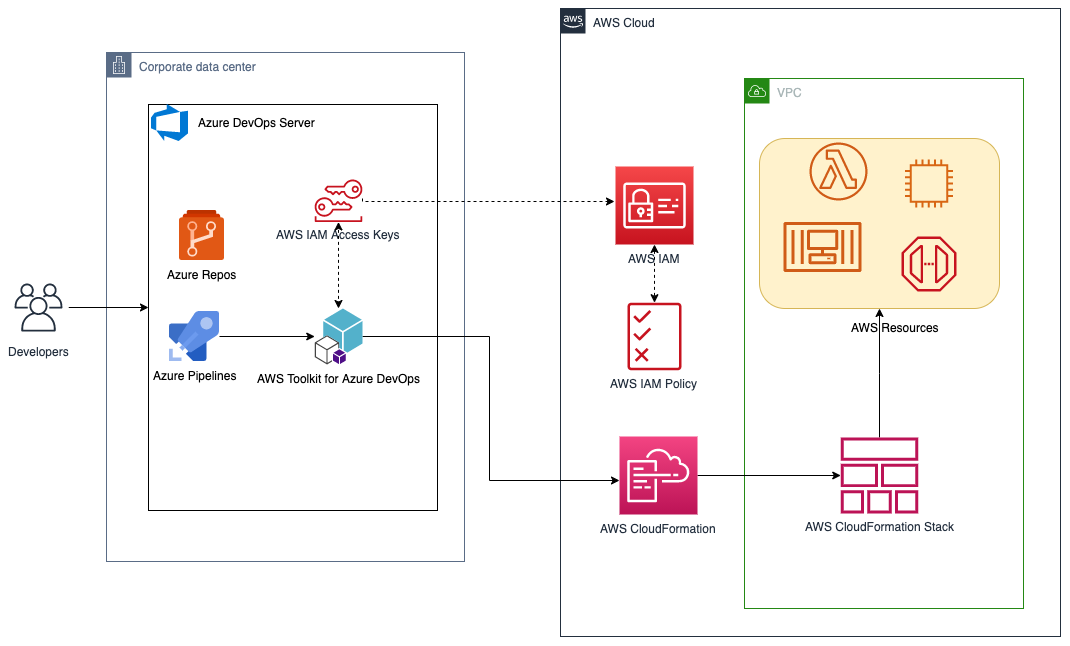\nFigure 1. Solution high-level overview\n\n#### **Prerequisites and Assumptions**\n\nYou will need to go through three main steps in order to set up your environment, which are summarized here and detailed in the toolkit’s [user guide](https://docs.aws.amazon.com/vsts/latest/userguide/getting-started.html#install-the-aws-tools-for-vsts-extension):\n\n- Install the toolkit into your Azure DevOps account or choose Download to install it on an on-premises server (Figure 2).\n- Create an IAM User and download its keys. Keep the [principle of least privilege](https://aws.amazon.com/blogs/security/techniques-for-writing-least-privilege-iam-policies/) in mind when associating the policy to your user.\n- Create a Service Connection for your project in Azure DevOps. Service connections are how the Azure DevOps tooling manages connecting and providing access to Azure resources. The Amazon Web Services Toolkit also provides a user interface to configure the Amazon Web Services credentials used by the service connection (Figure 3).\n\nIn addition to the above steps, you will need a sample Amazon Web Services CloudFormation template to use for testing the deployment such as [this sample template creating an EC2 instance](https://s3.eu-central-1.amazonaws.com/cloudformation-templates-eu-central-1/LAMP_Single_Instance.template). You can find more samples in the [Sample Templates page](https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/cfn-sample-templates.html) or get started with [authoring your own templates](https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/template-guide.html).\n\n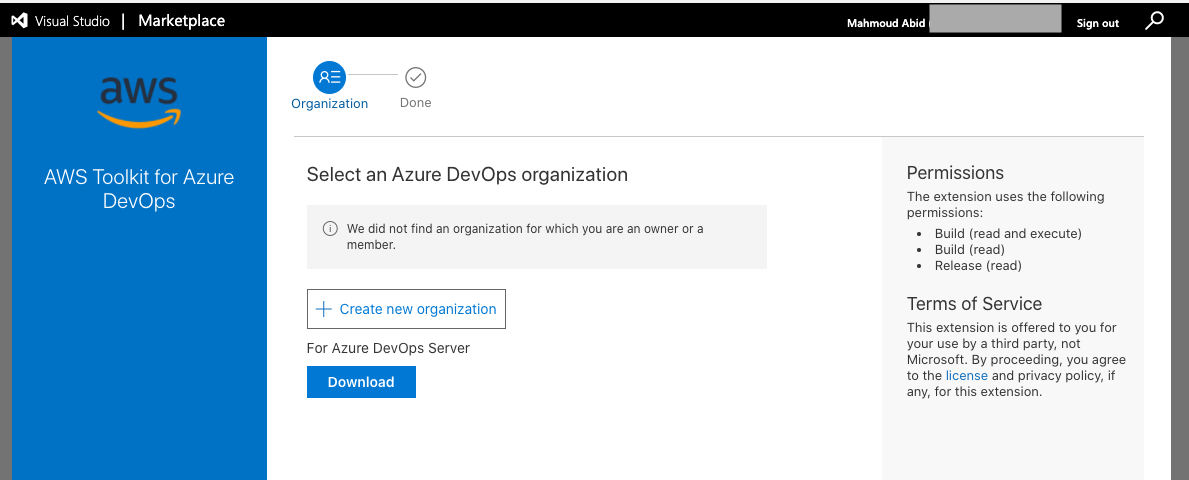\nFigure 2. Amazon Web Services Toolkit for Azure DevOps in the Visual Studio Marketplace\n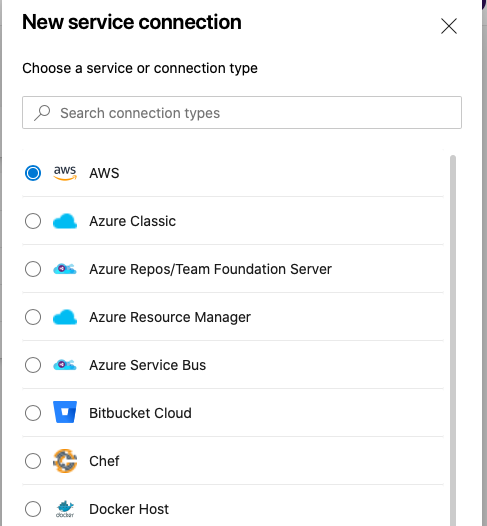\nFigure 3. A new Service Connection of type “Amazon Web Services” will appear after installing the extension\n\n#### **Model your CI/CD Pipeline to Automate Your Deployments on Amazon Web Services**\n\nOne common DevOps model is to have a CI/CD pipeline that deploys an application stack from one environment to another. This model typically includes a Development (or integration) account first, then Staging and finally a Production environment. Let me show you how to make some changes to the service connection configuration to apply this CI/CD model to an Azure DevOps pipeline.\n\nWe will create one service connection per Amazon Web Services account we want to deploy resources to. Figure 4 illustrates the updated solution to showcase multiple Amazon Web Services Accounts used within the same Azure DevOps pipeline.\n\n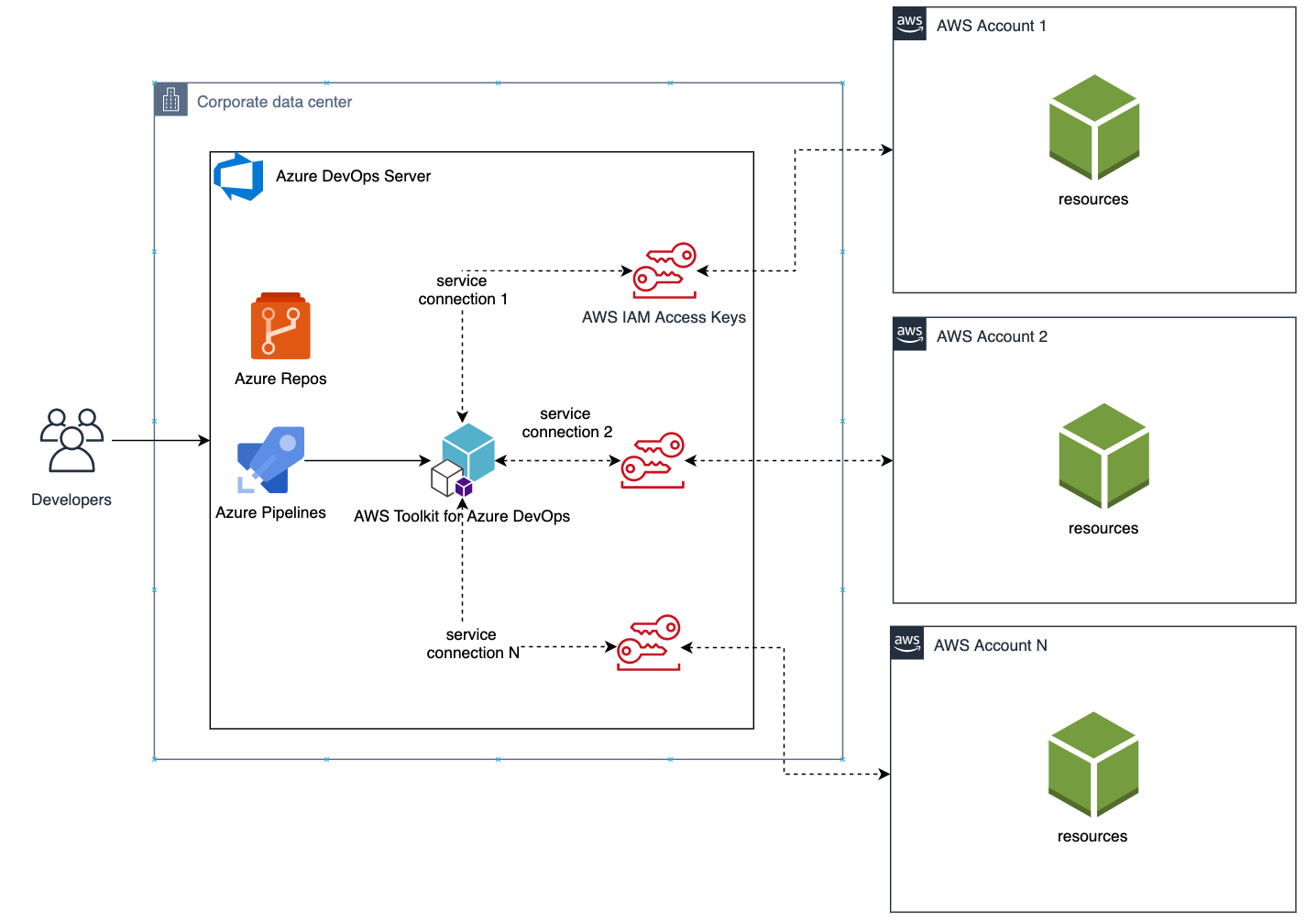\nFigure 4. Solution overview with multiple target Amazon Web Services accounts\n\nEach service connection will be configured to use a single, target Amazon Web Services account. This can be done in two ways:\n\n1. Create an IAM User for every Amazon Web Services target account and supply the access key ID and secret access key for that user.\n2. Alternatively, create one central IAM User and have it assume an IAM Role for every Amazon Web Services deployment target. The Amazon Web Services Toolkit extension enables you to select an IAM Role to assume. This IAM Role can be in the same Amazon Web Services account as the IAM User or in a different accounts as depicted in Figure 5.\n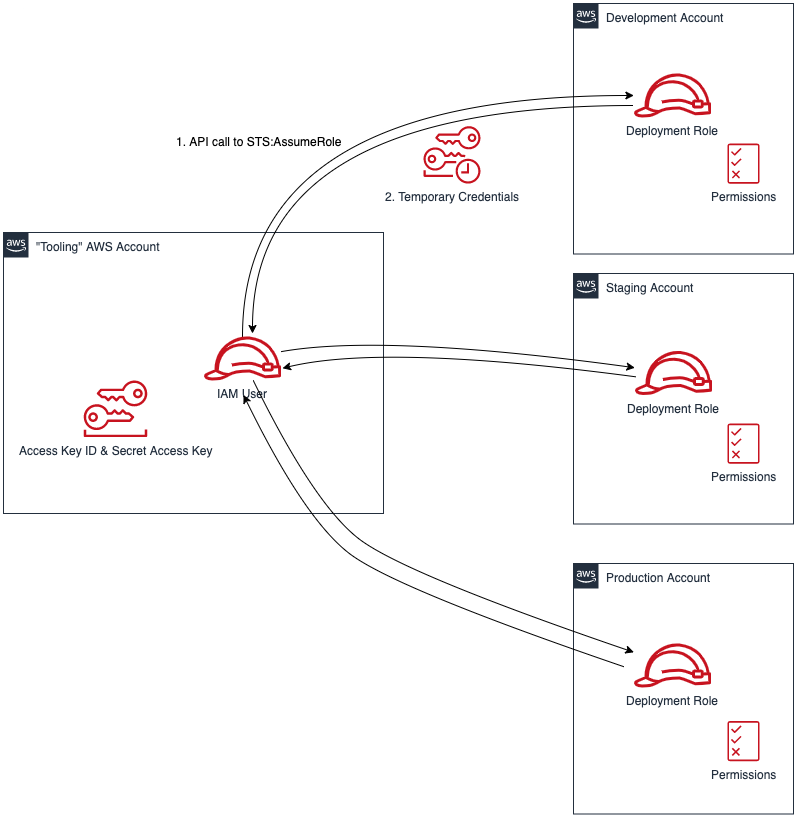\nFigure 5. Use a single IAM User to access all other accounts\n\n#### **Define Your Pipeline Tasks**\n\nOnce a service connection for your Amazon Web Services Account is created, you can now add a task to your pipeline that references the service connection created in the previous step. In the example below, I use the [CloudFormation Create/Update Stack task](https://docs.aws.amazon.com/vsts/latest/userguide/cloudformation-create-update.html) to deploy a CloudFormation stack using a template file named ```my-awscloudformation-template.yml```:\n\n```\nYAML\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Development-Deployment'\n inputs:\n awsCredentials: 'development-account'\n regionName: 'eu-central-1'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-change-set'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: 'development/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n```\n\nI used the service connection that I’ve called ```development-account``` and specified the other required information such as the ```templateFile``` path for the AWS CloudFormation template. I also specified the optional ```templateParametersFile``` path because I used [template parameters](https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/parameters-section-structure.html) in my template.\n\nA template parameters file is particularly useful if you need to use custom values in your CloudFormation templates that are different for each stack. This is a common case when deploying the same application stack to different environments (Development, Staging, and Production).\n\nThe task below will to deploy the same template to a Staging environment:\n\n```\nYAML\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Staging-Deployment'\n inputs:\n awsCredentials: 'staging-account'\n regionName: 'eu-central-1'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-changeset'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: 'staging/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n```\n\nThe differences between Development and Staging deployment tasks are the service connection name and template parameters file path used. Remember that each service connection points to a different Amazon Web Services account and the corresponding parameter values are specific to the target environment.\n\n#### **Use Azure DevOps Parameters to Switch Between Your Amazon Web Services Accounts**\n\nAzure DevOps lets you define reusable contents via pipeline templates and pass different variable values to them when defining the build tasks. You can leverage this functionality so that you easily replicate your deployment steps to your different environments.\n\nIn the pipeline template snippet below, I use three template parameters that are passed as input to my task definition:\n\n```\nYAML\n# File pipeline-templates/my-application.yml\n\nparameters:\n deploymentEnvironment: '' # development, staging, production, etc\n awsCredentials: '' # service connection name\n region: '' # the AWS region\n\nsteps:\n\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Staging-Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-changeset'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: '${{ parameters.deploymentEnvironment }}/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n```\n\nThis template can then be used when defining your pipeline with steps to deploy to the Development and Staging environments. The values passed to the parameters will control the target AWS Account the CloudFormation stack will be deployed to :\n\n```\nYAML\n# File development/pipeline.yml\n\ncontainer: amazon/aws-cli\n\ntrigger:\n branches:\n include:\n - master\n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: 'development'\n awsCredentials: 'deployment-development'\n region: 'eu-central-1'\n \n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: 'staging'\n awsCredentials: 'deployment-staging'\n region: 'eu-central-1'\n```\n\n#### **Putting it All Together**\n\nIn the snippet examples below, I defined an Azure DevOps pipeline template that builds a Docker image, pushes it to Amazon ECR (using the [ECR Push Task](https://docs.aws.amazon.com/vsts/latest/userguide/ecr-pushimage.html)) , creates/updates a stack from an Amazon Web Services CloudFormation template with a template parameter files, and finally runs a Amazon Web Services CLI command to list all Load Balancers using the [Amazon Web Services CLI Task](https://docs.aws.amazon.com/vsts/latest/userguide/aws-cli.html).\n\nThe template below can be reused across different Amazon Web Services accounts by simply switching the value of the defined parameters as described in the previous section.\n\nDefine a template containing your Amazon Web Services deployment steps:\n\n```\nYAML\n# File pipeline-templates/my-application.yml\n\nparameters:\n deploymentEnvironment: '' # development, staging, production, etc\n awsCredentials: '' # service connection name\n region: '' # the AWS region\n\nsteps:\n\n# Build a Docker image\n - task: Docker@1\n displayName: 'Build docker image'\n inputs:\n dockerfile: 'Dockerfile'\n imageName: 'my-application:${{parameters.deploymentEnvironment}}'\n\n# Push Docker Image to Amazon ECR\n - task: ECRPushImage@1\n displayName: 'Push image to ECR'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n sourceImageName: 'my-application'\n repositoryName: 'my-application'\n \n# Deploy AWS CloudFormation Stack\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: My Application Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-application'\n useChangeSet: true\n changeSetName: 'my-application-changeset'\n templateFile: 'cfn-templates/my-application-template.yml'\n templateParametersFile: '${{ parameters.deploymentEnvironment }}/my-application-parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n \n# Use AWS CLI to perform commands, e.g. list Load Balancers \n - task: AWSShellScript@1\n displayName: 'AWS CLI: List Elastic Load Balancers'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n scriptType: 'inline'\n inlineScript: 'aws elbv2 describe-load-balancers'\n```\n\nDefine a pipeline file for deploying to the Development account:\n\n```\nYAML\n# File development/azure-pipelines.yml\n\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'development'\n- name: awsCredentials\n value: 'deployment-development'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n - dev\n paths:\n include:\n - \"${{ variables.deploymentEnvironment }}/*\" \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n```\n\n(Optionally) Define a pipeline file for deploying to the Staging and Production accounts\n\n```\nYAML\n<p># File staging/azure-pipelines.yml</p>\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'staging'\n- name: awsCredentials\n value: 'deployment-staging'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n paths:\n include:\n - \"${{ variables.deploymentEnvironment }}/*\" \n \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n```\n\n```\nYAML\n# File production/azure-pipelines.yml\n\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'production'\n- name: awsCredentials\n value: 'deployment-production'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n paths:\n include:\n - \"${{ variables.deploymentEnvironment }}/*\" \n \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n```\n\n#### **Cleanup**\n\nAfter you have tested and verified your pipeline, you should remove any unused resources by deleting the CloudFormation stacks to avoid unintended account charges. You can [delete the stack manually from the Amazon Web Services Console](https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/cfn-console-delete-stack.html) or use your Azure DevOps pipeline by adding a [CloudFormationDeleteStack](https://docs.aws.amazon.com/vsts/latest/userguide/cloudformation-delete-stack.html) task:\n\n```\nYAML\n- task: CloudFormationDeleteStack@1\n displayName: 'Delete Stack: My Application Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-application' \n```\n \n#### **Conclusion**\n\nIn this post, I showed you how you can easily leverage the Amazon Web Services Toolkit for AzureDevOps extension to deploy resources to your Amazon Web Services account from Azure DevOps and Azure DevOps Server. The story does not end here. This extension integrates directly with others services as well, making it easy to build your pipelines around them:\n\n- AWSCLI – Interact with the AWSCLI (Windows hosts only)\n- Amazon Web Services Powershell Module – Interact with Amazon Web Services through powershell (Windows hosts only)\n- Beanstalk – Deploy ElasticBeanstalk applications\n- CodeDeploy – Deploy with CodeDeploy\n- CloudFormation – Create/Delete/Update CloudFormation stacks\n- ECR – Push an image to an ECR repository\n- Lambda – Deploy from S3, .net core applications, or any other language that builds on Azure DevOps\n- S3 – Upload/Download to/from S3 buckets\n- Secrets Manager – Create and retrieve secrets\n- SQS – Send SQS messages\n- SNS – Send SNS messages\n- Systems manager – Get/set parameters and run commands\n\nThe toolkit is an open-source project available in [GitHub](https://github.com/aws/aws-toolkit-azure-devops). We’d love to see your issues, feature requests, code reviews, pull requests, or any positive contribution coming up.\n\n##### **Author:**\n\n\n\n##### **Mahmoud Abid**\n\nMahmoud Abid is a Senior Customer Delivery Architect at Amazon Web Services. He focuses on designing technical solutions that solve complex business challenges for customers across EMEA. A builder at heart, Mahmoud has been designing large scale applications on Amazon Web Services since 2011 and, in his spare time, enjoys every DIY opportunity to build something at home or outdoors.\n\nTAGS: [Developer Tools](https://aws.amazon.com/blogs/devops/tag/developer-tools/), [DevOps](https://aws.amazon.com/blogs/devops/tag/devops/)","render":"<p>Many developers today seek to improve productivity by finding better ways to collaborate, enhance code quality and automate repetitive tasks. We hear from some of our customers that they would like to leverage services such as Amazon Web Services CloudFormation, Amazon Web Services CodeBuild and other <a href=\"https://aws.amazon.com/products/developer-tools/\" target=\"_blank\">Amazon Web Services Developer Tools</a> to manage their Amazon Web Services resources while continuing to use their existing CI/CD pipelines which they are familiar with. These services range from popular open-source solutions, such as Jenkins, to paid commercial solutions, such as Azure DevOps Server (formerly Team Foundation Server (TFS)).</p>\n<p>In this post, I will walk you through an example to leverage the <a href=\"https://aws.amazon.com/vsts/\" target=\"_blank\">Amazon Web Services Toolkit for Azure DevOps</a> to deploy your Infrastructure as Code templates, i.e. Amazon Web Services CloudFormation stacks, directly from your existing Azure DevOps build pipelines.</p>\n<p>The Amazon Web Services Toolkit for Azure DevOps is a free-to-use extension for hosted and on-premises Microsoft Azure DevOps that makes it easy to manage and deploy applications using Amazon Web Services. It integrates with many Amazon Web Services services, including Amazon S3, Amazon Web Services CodeDeploy, Amazon Web Services Lambda, Amazon Web Services CloudFormation, Amazon SQS and others. It can also run commands using the Amazon Web Services Tools for Windows PowerShell module as well as the Amazon Web Services CLI.</p>\n<h4><a id=\"Solution_Overview_6\"></a><strong>Solution Overview</strong></h4>\n<p>The solution described in this post consists of leveraging the Amazon Web Services Toolkit for Azure DevOps to manage resources on Amazon Web Services via Infrastructure as Code templates with Amazon Web Services CloudFormation:</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/b947b048154241d98d0ff360309bf90d_image.png\" alt=\"image.png\" /><br />\nFigure 1. Solution high-level overview</p>\n<h4><a id=\"Prerequisites_and_Assumptions_13\"></a><strong>Prerequisites and Assumptions</strong></h4>\n<p>You will need to go through three main steps in order to set up your environment, which are summarized here and detailed in the toolkit’s <a href=\"https://docs.aws.amazon.com/vsts/latest/userguide/getting-started.html#install-the-aws-tools-for-vsts-extension\" target=\"_blank\">user guide</a>:</p>\n<ul>\n<li>Install the toolkit into your Azure DevOps account or choose Download to install it on an on-premises server (Figure 2).</li>\n<li>Create an IAM User and download its keys. Keep the <a href=\"https://aws.amazon.com/blogs/security/techniques-for-writing-least-privilege-iam-policies/\" target=\"_blank\">principle of least privilege</a> in mind when associating the policy to your user.</li>\n<li>Create a Service Connection for your project in Azure DevOps. Service connections are how the Azure DevOps tooling manages connecting and providing access to Azure resources. The Amazon Web Services Toolkit also provides a user interface to configure the Amazon Web Services credentials used by the service connection (Figure 3).</li>\n</ul>\n<p>In addition to the above steps, you will need a sample Amazon Web Services CloudFormation template to use for testing the deployment such as <a href=\"https://s3.eu-central-1.amazonaws.com/cloudformation-templates-eu-central-1/LAMP_Single_Instance.template\" target=\"_blank\">this sample template creating an EC2 instance</a>. You can find more samples in the <a href=\"https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/cfn-sample-templates.html\" target=\"_blank\">Sample Templates page</a> or get started with <a href=\"https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/template-guide.html\" target=\"_blank\">authoring your own templates</a>.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/fa3e4fb3f4214466b3e7d781ab8d389c_image.png\" alt=\"image.png\" /><br />\nFigure 2. Amazon Web Services Toolkit for Azure DevOps in the Visual Studio Marketplace<br />\n<img src=\"https://dev-media.amazoncloud.cn/d4258157ff30424fa28ed84adf61840d_image.png\" alt=\"image.png\" /><br />\nFigure 3. A new Service Connection of type “Amazon Web Services” will appear after installing the extension</p>\n<h4><a id=\"Model_your_CICD_Pipeline_to_Automate_Your_Deployments_on_Amazon_Web_Services_28\"></a><strong>Model your CI/CD Pipeline to Automate Your Deployments on Amazon Web Services</strong></h4>\n<p>One common DevOps model is to have a CI/CD pipeline that deploys an application stack from one environment to another. This model typically includes a Development (or integration) account first, then Staging and finally a Production environment. Let me show you how to make some changes to the service connection configuration to apply this CI/CD model to an Azure DevOps pipeline.</p>\n<p>We will create one service connection per Amazon Web Services account we want to deploy resources to. Figure 4 illustrates the updated solution to showcase multiple Amazon Web Services Accounts used within the same Azure DevOps pipeline.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/301344b2b5104a8ab542cfa48022057a_image.png\" alt=\"image.png\" /><br />\nFigure 4. Solution overview with multiple target Amazon Web Services accounts</p>\n<p>Each service connection will be configured to use a single, target Amazon Web Services account. This can be done in two ways:</p>\n<ol>\n<li>Create an IAM User for every Amazon Web Services target account and supply the access key ID and secret access key for that user.</li>\n<li>Alternatively, create one central IAM User and have it assume an IAM Role for every Amazon Web Services deployment target. The Amazon Web Services Toolkit extension enables you to select an IAM Role to assume. This IAM Role can be in the same Amazon Web Services account as the IAM User or in a different accounts as depicted in Figure 5.<br />\n<img src=\"https://dev-media.amazoncloud.cn/ab831e06d6a744be8aec10df0a7d43f3_image.png\" alt=\"image.png\" /><br />\nFigure 5. Use a single IAM User to access all other accounts</li>\n</ol>\n<h4><a id=\"Define_Your_Pipeline_Tasks_44\"></a><strong>Define Your Pipeline Tasks</strong></h4>\n<p>Once a service connection for your Amazon Web Services Account is created, you can now add a task to your pipeline that references the service connection created in the previous step. In the example below, I use the <a href=\"https://docs.aws.amazon.com/vsts/latest/userguide/cloudformation-create-update.html\" target=\"_blank\">CloudFormation Create/Update Stack task</a> to deploy a CloudFormation stack using a template file named <code>my-awscloudformation-template.yml</code>:</p>\n<pre><code class=\"lang-\">YAML\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Development-Deployment'\n inputs:\n awsCredentials: 'development-account'\n regionName: 'eu-central-1'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-change-set'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: 'development/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n</code></pre>\n<p>I used the service connection that I’ve called <code>development-account</code> and specified the other required information such as the <code>templateFile</code> path for the AWS CloudFormation template. I also specified the optional <code>templateParametersFile</code> path because I used <a href=\"https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/parameters-section-structure.html\" target=\"_blank\">template parameters</a> in my template.</p>\n<p>A template parameters file is particularly useful if you need to use custom values in your CloudFormation templates that are different for each stack. This is a common case when deploying the same application stack to different environments (Development, Staging, and Production).</p>\n<p>The task below will to deploy the same template to a Staging environment:</p>\n<pre><code class=\"lang-\">YAML\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Staging-Deployment'\n inputs:\n awsCredentials: 'staging-account'\n regionName: 'eu-central-1'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-changeset'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: 'staging/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n</code></pre>\n<p>The differences between Development and Staging deployment tasks are the service connection name and template parameters file path used. Remember that each service connection points to a different Amazon Web Services account and the corresponding parameter values are specific to the target environment.</p>\n<h4><a id=\"Use_Azure_DevOps_Parameters_to_Switch_Between_Your_Amazon_Web_Services_Accounts_88\"></a><strong>Use Azure DevOps Parameters to Switch Between Your Amazon Web Services Accounts</strong></h4>\n<p>Azure DevOps lets you define reusable contents via pipeline templates and pass different variable values to them when defining the build tasks. You can leverage this functionality so that you easily replicate your deployment steps to your different environments.</p>\n<p>In the pipeline template snippet below, I use three template parameters that are passed as input to my task definition:</p>\n<pre><code class=\"lang-\">YAML\n# File pipeline-templates/my-application.yml\n\nparameters:\n deploymentEnvironment: '' # development, staging, production, etc\n awsCredentials: '' # service connection name\n region: '' # the AWS region\n\nsteps:\n\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: Staging-Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-stack-name'\n useChangeSet: true\n changeSetName: 'my-stack-name-changeset'\n templateFile: 'my-aws-cloudformation-template.yml'\n templateParametersFile: '${{ parameters.deploymentEnvironment }}/parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n</code></pre>\n<p>This template can then be used when defining your pipeline with steps to deploy to the Development and Staging environments. The values passed to the parameters will control the target AWS Account the CloudFormation stack will be deployed to :</p>\n<pre><code class=\"lang-\">YAML\n# File development/pipeline.yml\n\ncontainer: amazon/aws-cli\n\ntrigger:\n branches:\n include:\n - master\n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: 'development'\n awsCredentials: 'deployment-development'\n region: 'eu-central-1'\n \n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: 'staging'\n awsCredentials: 'deployment-staging'\n region: 'eu-central-1'\n</code></pre>\n<h4><a id=\"Putting_it_All_Together_146\"></a><strong>Putting it All Together</strong></h4>\n<p>In the snippet examples below, I defined an Azure DevOps pipeline template that builds a Docker image, pushes it to Amazon ECR (using the <a href=\"https://docs.aws.amazon.com/vsts/latest/userguide/ecr-pushimage.html\" target=\"_blank\">ECR Push Task</a>) , creates/updates a stack from an Amazon Web Services CloudFormation template with a template parameter files, and finally runs a Amazon Web Services CLI command to list all Load Balancers using the <a href=\"https://docs.aws.amazon.com/vsts/latest/userguide/aws-cli.html\" target=\"_blank\">Amazon Web Services CLI Task</a>.</p>\n<p>The template below can be reused across different Amazon Web Services accounts by simply switching the value of the defined parameters as described in the previous section.</p>\n<p>Define a template containing your Amazon Web Services deployment steps:</p>\n<pre><code class=\"lang-\">YAML\n# File pipeline-templates/my-application.yml\n\nparameters:\n deploymentEnvironment: '' # development, staging, production, etc\n awsCredentials: '' # service connection name\n region: '' # the AWS region\n\nsteps:\n\n# Build a Docker image\n - task: Docker@1\n displayName: 'Build docker image'\n inputs:\n dockerfile: 'Dockerfile'\n imageName: 'my-application:${{parameters.deploymentEnvironment}}'\n\n# Push Docker Image to Amazon ECR\n - task: ECRPushImage@1\n displayName: 'Push image to ECR'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n sourceImageName: 'my-application'\n repositoryName: 'my-application'\n \n# Deploy AWS CloudFormation Stack\n- task: CloudFormationCreateOrUpdateStack@1\n displayName: 'Create/Update Stack: My Application Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-application'\n useChangeSet: true\n changeSetName: 'my-application-changeset'\n templateFile: 'cfn-templates/my-application-template.yml'\n templateParametersFile: '${{ parameters.deploymentEnvironment }}/my-application-parameters.json'\n captureStackOutputs: asVariables\n captureAsSecuredVars: false\n \n# Use AWS CLI to perform commands, e.g. list Load Balancers \n - task: AWSShellScript@1\n displayName: 'AWS CLI: List Elastic Load Balancers'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n scriptType: 'inline'\n inlineScript: 'aws elbv2 describe-load-balancers'\n</code></pre>\n<p>Define a pipeline file for deploying to the Development account:</p>\n<pre><code class=\"lang-\">YAML\n# File development/azure-pipelines.yml\n\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'development'\n- name: awsCredentials\n value: 'deployment-development'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n - dev\n paths:\n include:\n - "${{ variables.deploymentEnvironment }}/*" \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n</code></pre>\n<p>(Optionally) Define a pipeline file for deploying to the Staging and Production accounts</p>\n<pre><code class=\"lang-\">YAML\n<p># File staging/azure-pipelines.yml</p>\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'staging'\n- name: awsCredentials\n value: 'deployment-staging'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n paths:\n include:\n - "${{ variables.deploymentEnvironment }}/*" \n \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n</code></pre>\n<pre><code class=\"lang-\">YAML\n# File production/azure-pipelines.yml\n\ncontainer: amazon/aws-cli\n\nvariables:\n- name: deploymentEnvironment\n value: 'production'\n- name: awsCredentials\n value: 'deployment-production'\n- name: region\n value: 'eu-central-1' \n\ntrigger:\n branches:\n include:\n - master\n paths:\n include:\n - "${{ variables.deploymentEnvironment }}/*" \n \n \nsteps:\n- template: ../pipeline-templates/my-application.yml \n parameters:\n deploymentEnvironment: ${{ variables.deploymentEnvironment }}\n awsCredentials: ${{ variables.awsCredentials }}\n region: ${{ variables.region }}\n</code></pre>\n<h4><a id=\"Cleanup_301\"></a><strong>Cleanup</strong></h4>\n<p>After you have tested and verified your pipeline, you should remove any unused resources by deleting the CloudFormation stacks to avoid unintended account charges. You can <a href=\"https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/cfn-console-delete-stack.html\" target=\"_blank\">delete the stack manually from the Amazon Web Services Console</a> or use your Azure DevOps pipeline by adding a <a href=\"https://docs.aws.amazon.com/vsts/latest/userguide/cloudformation-delete-stack.html\" target=\"_blank\">CloudFormationDeleteStack</a> task:</p>\n<pre><code class=\"lang-\">YAML\n- task: CloudFormationDeleteStack@1\n displayName: 'Delete Stack: My Application Deployment'\n inputs:\n awsCredentials: '${{ parameters.awsCredentials }}'\n regionName: '${{ parameters.region }}'\n stackName: 'my-application' \n</code></pre>\n<h4><a id=\"Conclusion_315\"></a><strong>Conclusion</strong></h4>\n<p>In this post, I showed you how you can easily leverage the Amazon Web Services Toolkit for AzureDevOps extension to deploy resources to your Amazon Web Services account from Azure DevOps and Azure DevOps Server. The story does not end here. This extension integrates directly with others services as well, making it easy to build your pipelines around them:</p>\n<ul>\n<li>AWSCLI – Interact with the AWSCLI (Windows hosts only)</li>\n<li>Amazon Web Services Powershell Module – Interact with Amazon Web Services through powershell (Windows hosts only)</li>\n<li>Beanstalk – Deploy ElasticBeanstalk applications</li>\n<li>CodeDeploy – Deploy with CodeDeploy</li>\n<li>CloudFormation – Create/Delete/Update CloudFormation stacks</li>\n<li>ECR – Push an image to an ECR repository</li>\n<li>Lambda – Deploy from S3, .net core applications, or any other language that builds on Azure DevOps</li>\n<li>S3 – Upload/Download to/from S3 buckets</li>\n<li>Secrets Manager – Create and retrieve secrets</li>\n<li>SQS – Send SQS messages</li>\n<li>SNS – Send SNS messages</li>\n<li>Systems manager – Get/set parameters and run commands</li>\n</ul>\n<p>The toolkit is an open-source project available in <a href=\"https://github.com/aws/aws-toolkit-azure-devops\" target=\"_blank\">GitHub</a>. We’d love to see your issues, feature requests, code reviews, pull requests, or any positive contribution coming up.</p>\n<h5><a id=\"Author_334\"></a><strong>Author:</strong></h5>\n<p><img src=\"https://dev-media.amazoncloud.cn/1dbdd292f02d4167abf4a5b4ff0b79a0_image.png\" alt=\"image.png\" /></p>\n<h5><a id=\"Mahmoud_Abid_338\"></a><strong>Mahmoud Abid</strong></h5>\n<p>Mahmoud Abid is a Senior Customer Delivery Architect at Amazon Web Services. He focuses on designing technical solutions that solve complex business challenges for customers across EMEA. A builder at heart, Mahmoud has been designing large scale applications on Amazon Web Services since 2011 and, in his spare time, enjoys every DIY opportunity to build something at home or outdoors.</p>\n<p>TAGS: <a href=\"https://aws.amazon.com/blogs/devops/tag/developer-tools/\" target=\"_blank\">Developer Tools</a>, <a href=\"https://aws.amazon.com/blogs/devops/tag/devops/\" target=\"_blank\">DevOps</a></p>\n"}
Use the Amazon Toolkit for Azure DevOps to automate your deployments to Amazon
海外精选
海外精选的内容汇集了全球优质的亚马逊云科技相关技术内容。同时,内容中提到的“AWS”
是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。

 0
0 0
0亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
目录
亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
亚马逊云科技解决方案
基于行业客户应用场景及技术领域的解决方案
联系专家
0
目录
 分享
分享 点赞
点赞 收藏
收藏 目录
目录立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
