{"value":"Watts S. Humphrey, the father of Software Quality, had famously quipped, “Every business is a software business”. Software is indeed integral to any industry. The engineers who create software are also responsible for making sure that the underlying code adheres to industry and organizational standards, are performant, and are absolved of any security vulnerabilities that could make them susceptible to attack.\n\nTraditionally, security testing has been the forte of a specialized security testing team, who would conduct their tests toward the end of the Software Development lifecycle (SDLC). The adoption of [DevSecOps](https://aws.amazon.com/blogs/security/tag/devsecops/) practices meant that security became a shared responsibility between the development and security teams. Now, development teams can, on their own or as advised by their security team, setup and configure various code scanning tools to detect security vulnerabilities much earlier in the software delivery process (aka “[Shift Left](https://www.drdobbs.com/shift-left-testing/184404768)”). Meanwhile, the practice of Static code analysis and security application testing (SAST) has become a standard part of the SDLC. Furthermore, it’s imperative that the development teams expect SAST tools that are easy to set-up, seamlessly fit into their DevOps infrastructure, and can be configured without requiring assistance from security or DevOps experts.\n\nIn this post, we’ll demonstrate how you can leverage [Amazon CodeGuru](https://aws.amazon.com/codeguru/) Reviewer Command Line Interface (CLI) to integrate CodeGuru Reviewer into your Jenkins Continuous Integration & Continuous Delivery (CI/CD) pipeline. Note that the solution isn’t limited to Jenkins, and it would be equally useful with any other build automation tool. Moreover, it can be integrated at any stage of your SDLC as part of the White-box testing. For example, you can integrate the [CodeGuru Reviewer CLI](https://docs.aws.amazon.com/cli/latest/reference/codeguru-reviewer/index.html) as part of your software development process, as well as run it on your dev machine before committing the code.\n\nLaunched in 2020, CodeGuru Reviewer utilizes machine learning (ML) and automated reasoning to identify security vulnerabilities, inefficient uses of AWS APIs and SDKs, as well as other common coding errors. CodeGuru Reviewer employs a growing set of [detectors](https://docs.aws.amazon.com/codeguru/detector-library/) for Java and Python to provide recommendations via the [AWS Console](https://aws.amazon.com/console/). Customers that leverage the CodeGuru Reviewer CLI within a CI/CD pipeline also receive recommendations in a machine-readable JSON format, as well as HTML.\n\nCodeGuru Reviewer offers native integration with Source Code Management (SCM) systems, such as GitHub, BitBucket, and [AWS CodeCommit](https://aws.amazon.com/codecommit/). However, it can be used with any SCM via its CLI. The CodeGuru Reviewer CLI is a shim layer on top of the [AWS Command Line Interface (AWS CLI)](https://aws.amazon.com/cli/) that simplifies the interaction with the tool by handling the uploading of artifacts, triggering of the analysis, and fetching of the results, all in a single command.\n\nMany customers, including Mastercard, are benefiting from this new CodeGuru Reviewer CLI.\n\n“During one of our technical retrospectives, we noticed the need to integrate Amazon CodeGuru recommendations in our build pipelines hosted on Jenkins. Not all our developers can run or check CodeGuru recommendations through the AWS console. Incorporating CodeGuru CLI in our build pipelines acts as an important quality gate and ensures that our developers can immediately fix critical issues.”\n *Claudio Frattari, Lead DevOps at Mastercard*\n\n### **Solution overview**\nThe application deployment workflow starts by placing the application code on a GitHub SCM. To automate the scenario, we have added GitHub to the Jenkins project under the “Source Code” section. We chose the GitHub option, which would clone the chosen GitHub repository in the Jenkins local workspace directory.\n\nIn the build stage of the pipeline (see Figure 1), we configure the appropriate build tool to perform the code build and security analysis. In this example, we will be using [Maven](https://maven.apache.org/) as the build tool.\n\n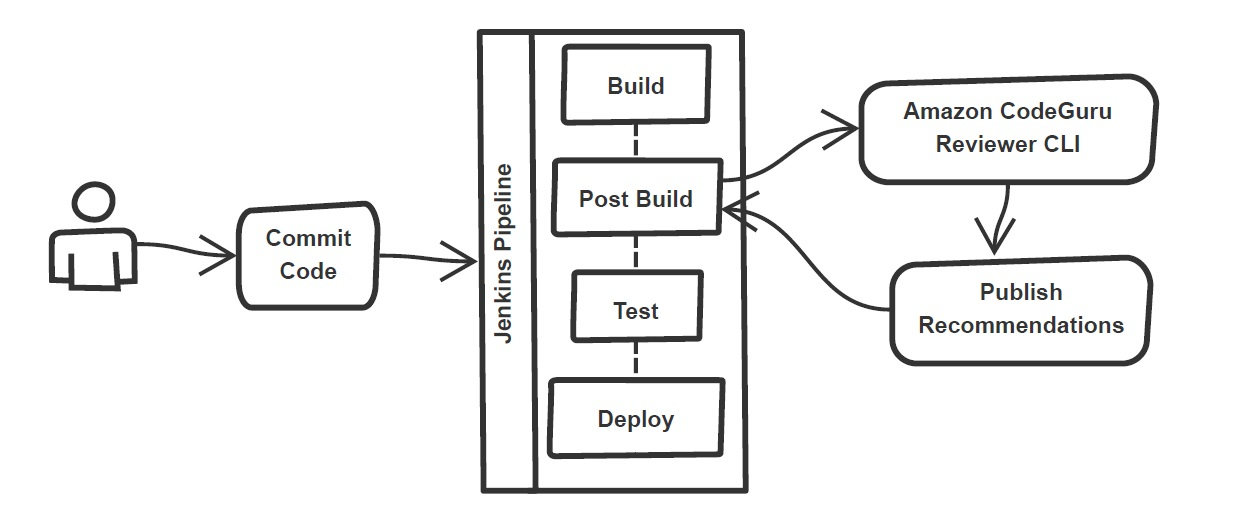\n\nFigure 1: Jenkins pipeline with Amazon CodeGuru Reviewer\n\nIn the post-build stage, we configure the CodeGuru Reviewer CLI to generate the recommendations based on the review.\n\nLastly, in the concluding stage of the pipeline, we’ll be analyzing the JSON results using [jq](https://stedolan.github.io/jq/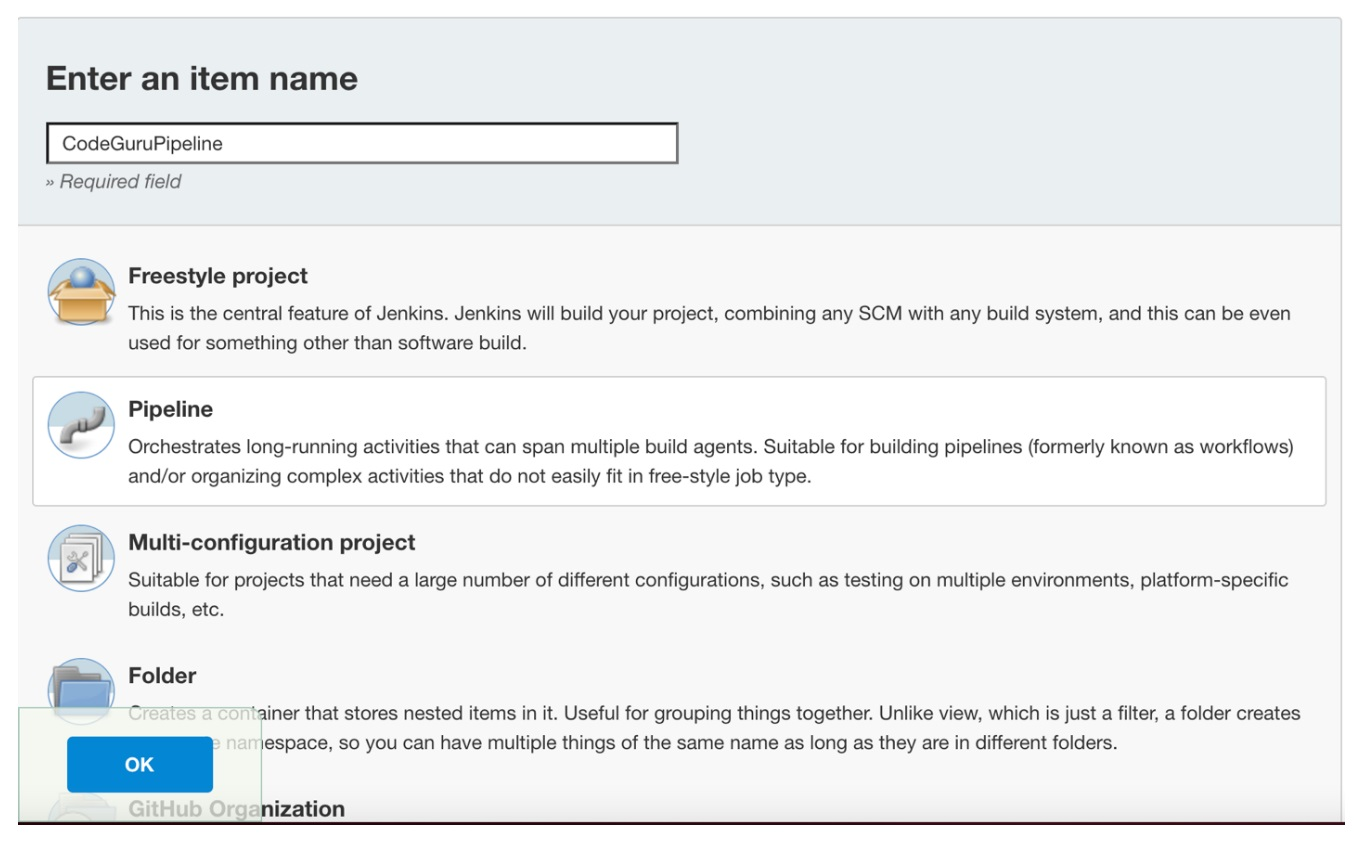) – a lightweight and flexible command-line JSON processor, and then failing the Jenkins job if we encounter observations that are of a “Critical” severity.\n\nJenkins will trigger the “CodeGuru Reviewer” (see Figure 1) based review process in the post-build stage, i.e., after the build finishes. Furthermore, you can configure other stages, such as automated testing or deployment, after this stage. Additionally, passing the location of the build artifacts to the CLI lets CodeGuru Reviewer perform a more in-depth security analysis. Build artifacts are either directories containing jar files (e.g., *build/lib for Gradle or /target* for Maven) or directories containing class hierarchies (e.g., *build/classes/java/main* for Gradle).\n\n### **Walkthrough**\nNow that we have an overview of the workflow, let’s dive deep and walk you through the following steps in detail:\n\n1. Installing the CodeGuru Reviewer CLI\n2. Creating a Jenkins pipeline job\n3. Reviewing the CodeGuru Reviewer recommendations\n4. Configuring CodeGuru Reviewer CLI’s additional options\n\n### **1. Installing the CodeGuru CLI Wrapper**\n#### **a. Prerequisites**\nTo run the CLI, we must have Git, Java, Maven, and the AWS CLI installed. Verify that they’re installed on our machine by running the following commands:\n\nBash\n```\njava -version \nmvn --version \naws --version \ngit –-version\n```\n\nIf they aren’t installed, then download and install Java [here](https://aws.amazon.com/corretto/) (Amazon Corretto is a no-cost, multiplatform, production-ready distribution of the Open Java Development Kit), Maven from [here](https://maven.apache.org/download.cgi), and Git from [here](https://git-scm.com/downloads). Instructions for installing AWS CLI are available [here](https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html).\n\nWe would need to create an [Amazon Simple Storage Service (Amazon S3) ](https://aws.amazon.com/s3/)bucket with the prefix codeguru-reviewer-. Note that the bucket name must begin with the mentioned prefix, since we have used the name pattern in the following [AWS Identity and Access Management (IAM)](https://aws.amazon.com/iam/) permissions, and CodeGuru Reviewer expects buckets to begin with this prefix. Refer to the following section 4(a) “Specifying S3 bucket name” for more details.\n\nFurthermore, we’ll need working credentials on our machine to interact with our [AWS account](https://aws.amazon.com/premiumsupport/knowledge-center/create-and-activate-aws-account/). Learn more about setting up credentials for AWS [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-configure.html). You can find the minimal permissions to run the CodeGuru Reviewer CLI as follows.\n\n#### **b. Required Permissions**\nTo use the CodeGuru Reviewer CLI, we need at least the following AWS IAM permissions, attached to an AWS IAM User or an AWS IAM role:\n\nJSON\n```\n{\n \"Version\": \"2012-10-17\",\n \"Statement\": [\n {\n \"Action\": [\n \"codeguru-reviewer:ListRepositoryAssociations\",\n \"codeguru-reviewer:AssociateRepository\",\n \"codeguru-reviewer:DescribeRepositoryAssociation\",\n \"codeguru-reviewer:CreateCodeReview\",\n \"codeguru-reviewer:DescribeCodeReview\",\n \"codeguru-reviewer:ListRecommendations\",\n \"iam:CreateServiceLinkedRole\"\n ],\n \"Resource\": \"*\",\n \"Effect\": \"Allow\"\n },\n {\n \"Action\": [\n \"s3:CreateBucket\",\n \"s3:GetBucket*\",\n \"s3:List*\",\n \"s3:GetObject\",\n \"s3:PutObject\",\n \"s3:DeleteObject\"\n ],\n \"Resource\": [\n \"arn:aws:s3:::codeguru-reviewer-*\",\n \"arn:aws:s3:::codeguru-reviewer-*/*\"\n ],\n \"Effect\": \"Allow\"\n }\n ]\n}\n```\n#### **c. CLI installation**\nPlease download the latest version of the CodeGuru Reviewer CLI available at GitHub. Then, run the following commands in sequence:\n\nBash\n```\ncurl -OL https://github.com/aws/aws-codeguru-cli/releases/download/0.0.1/aws-codeguru-cli.zip\nunzip aws-codeguru-cli.zip\nexport PATH=$PATH:./aws-codeguru-cli/bin\n```\n#### **d. Using the CLI**\nThe CodeGuru Reviewer CLI only has one required parameter –root-dir (or just -r) to specify to the local directory that should be analyzed. Furthermore, the –src option can be used to specify one or more files in this directory that contain the source code that should be analyzed. In turn, for Java applications, the –build option can be used to specify one or more build directories.\n\nFor a demonstration, we’ll analyze the demo application. This will make sure that we’re all set for when we leverage the CLI in Jenkins. To proceed, first we download and install the sample application, as follows:\n\nBash\n```\ngit clone https://github.com/aws-samples/amazon-codeguru-reviewer-sample-app\ncd amazon-codeguru-reviewer-sample-app\nmvn clean compile\n```\nNow that we have built our demo application, we can use the aws-codeguru-cli CLI command that we added to the path to trigger the code scan:\n\nBash\n```\naws-codeguru-cli --root-dir ./ --build target/classes --src src --output ./output\n```\nFor additional assistance on the CLI command, reference the readme [here](https://github.com/aws/aws-codeguru-cli).\n### **2. Creating a Jenkins Pipeline job**\nCodeGuru Reviewer can be integrated in a Jenkins Pipeline as well as a Freestyle project. In this example, we’re leveraging a Pipeline.\n\n#### **a. Pipeline Job Configuration**\n1. Log in to Jenkins, choose “New Item”, then select “Pipeline” option.\n2. Enter a name for the project (for example, “CodeGuruPipeline”), and choose OK.\n\n\n\nFigure 2: Creating a new Jenkins pipeline\n\n3. On the “Project configuration” page, scroll down to the bottom and find your pipeline. In the pipeline script, paste the following script (or use your own Jenkinsfile). The following example is a valid Jenkinsfile to integrate CodeGuru Reviewer with a project built using Maven.\n```\npipeline {\n agent any\n stages {\n stage('Build') {\n steps {\n // Get code from a GitHub repository\n git clone https://github.com/aws-samples/amazon-codeguru-reviewer-java-detectors.git\n\n // Run Maven on a Unix agent\n sh \"mvn clean compile\"\n\n // To run Maven on a Windows agent, use following\n // bat \"mvn -Dmaven.test.failure.ignore=true clean package\"\n }\n }\n stage('CodeGuru Reviewer') {\n steps{\n sh 'ls -lsa *'\n sh 'pwd'\n // Here we’re setting an absolute path, but we can \n // also use JENKINS environment variables\n sh '''\n export BASE=/var/jenkins_home/workspace/CodeGuruPipeline/amazon-codeguru-reviewer-java-detectors\n export SRC=${BASE}/src\n export OUTPUT = ./output\n /home/codeguru/aws-codeguru-cli/bin/aws-codeguru-cli --root-dir $BASE --build $BASE/target/classes --src $SRC --output $OUTPUT -c $GIT_PREVIOUS_COMMIT:$GIT_COMMIT --no-prompt\n '''\n }\n } \n stage('Checking findings'){\n steps{\n // In this example we are stopping our pipline on \n // detecting Critical findings. We are using jq \n // to count occurrences of Critical severity \n sh '''\n CNT = $(cat ./output/recommendations.json |jq '.[] | select(.severity==\"Critical\")|.severity' | wc -l)'\n if (( $CNT > 0 )); then\n echo \"Critical findings discovered. Failing.\"\n exit 1\n fi\n '''\n }\n }\n }\n}\n```\n4. Save the configuration and select “Build now” on the side bar to trigger the build process (see Figure 3).\n\n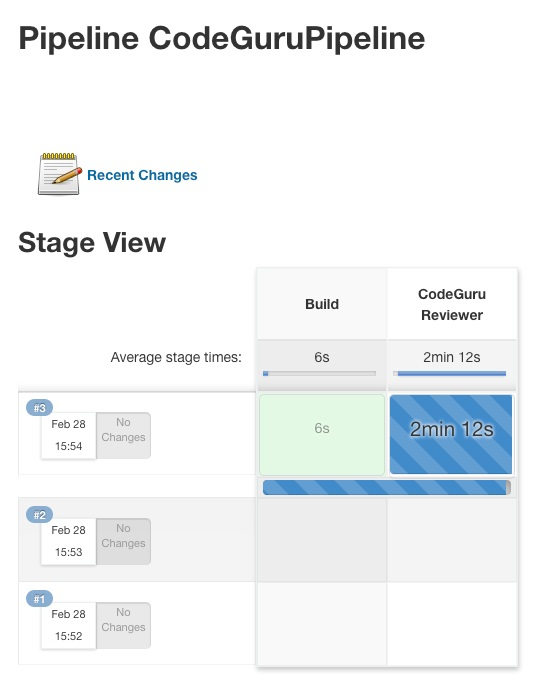\n\nFigure 3: Jenkins pipeline in triggered state\n\n### **3. Reviewing the CodeGuru Reviewer recommendations**\n\nOnce the build process is finished, you can view the review results from CodeGuru Reviewer by selecting the Jenkins build history for the most recent build job. Then, browse to Workspace output. The output is available in JSON and HTML formats (Figure 4).\n\n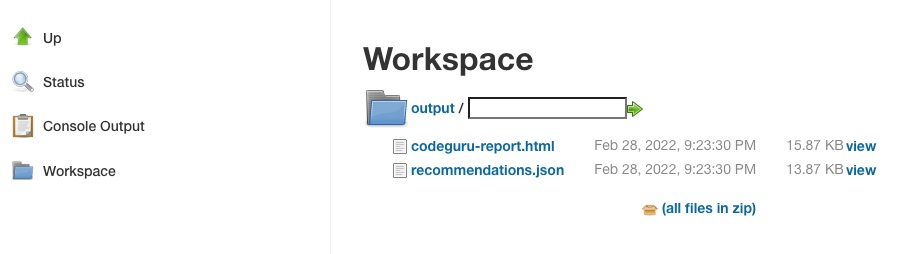\n\nFigure 4: CodeGuru CLI Output\n\nSnippets from the HTML and JSON reports are displayed in Figure 5 and 6 respectively.\n\nIn this example, our pipeline analyzes the JSON results with jq based on severity equal to critical and failing the job if there are any critical findings. Note that this output path is set with the –output option. For instance, the pipeline will fail on noticing the “critical” finding at Line 67 of the EventHandler.java class (Figure 5), flagged due to use of an insecure code. Till the time the code is remediated, the pipeline would prevent the code deployment. The vulnerability could have gone to production undetected, in absence of the tool.\n\n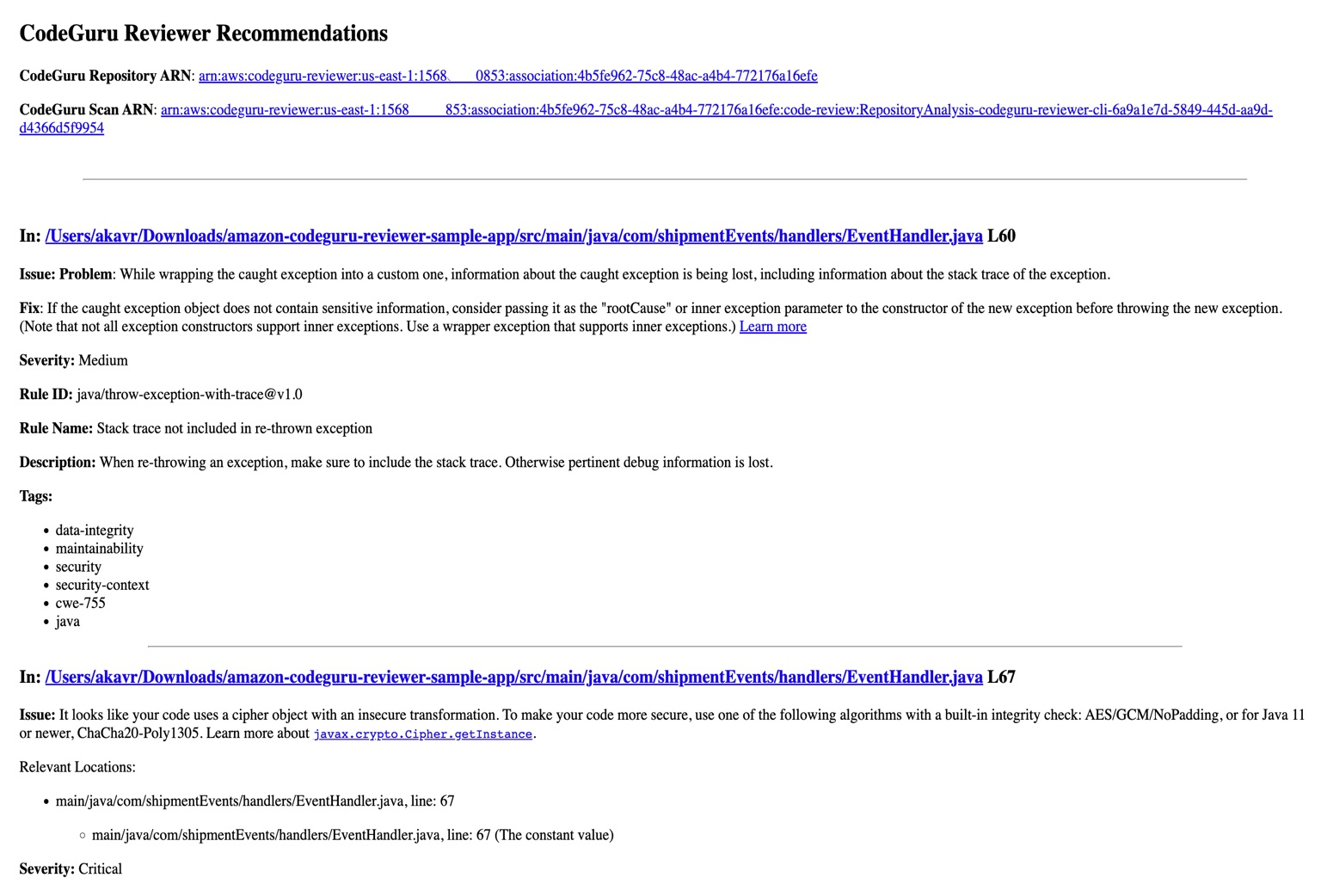\n\nFigure 5: CodeGuru HTML Report\n\n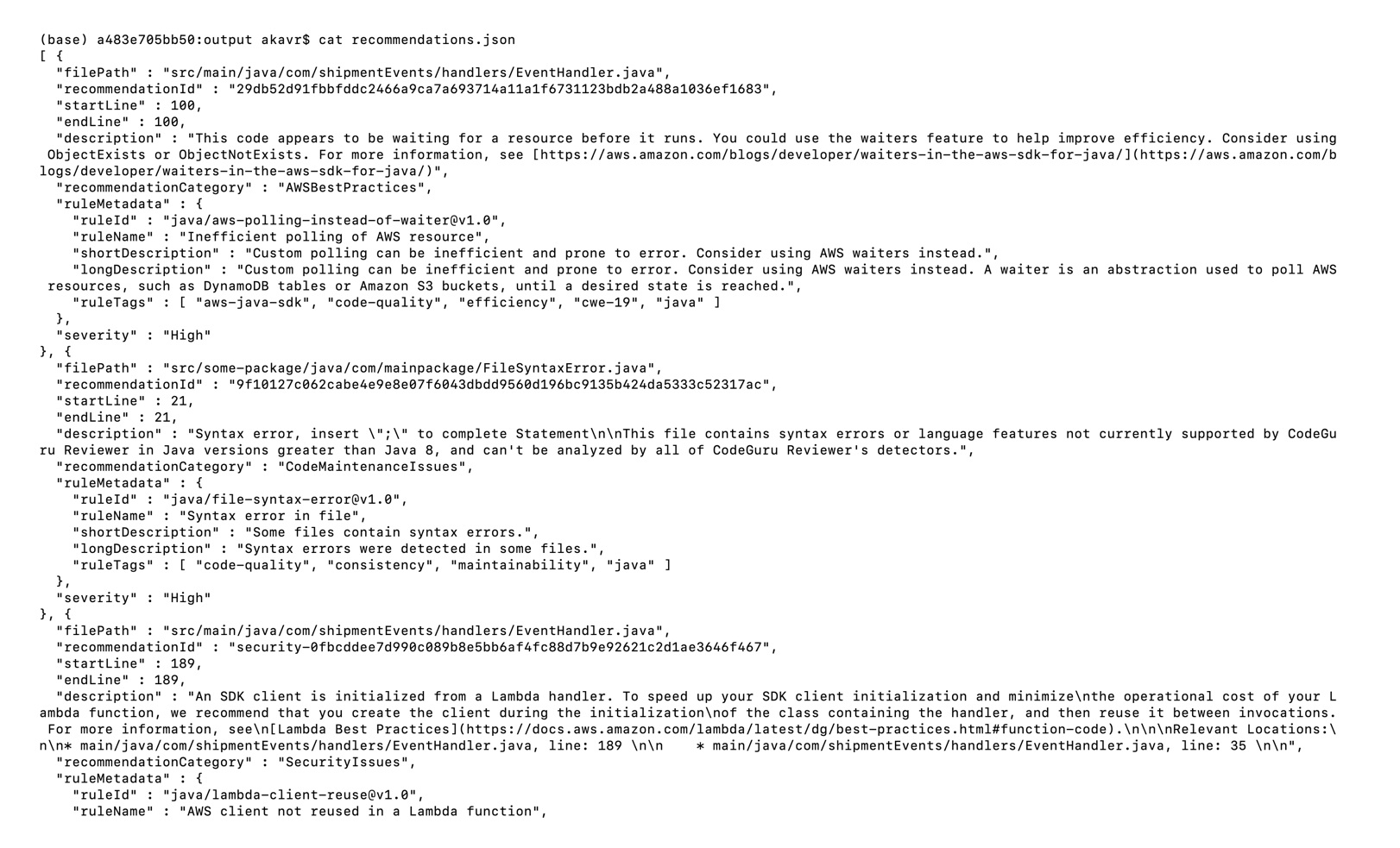\n\nFigure 6: CodeGuru JSON recommendations\n\n### **4.Configuring CodeGuru Reviewer CLI’s additional options**\n#### **a. Specifying Amazon S3 bucket name and policy**\nCodeGuru Reviewer needs one [Amazon S3 bucket](https://docs.aws.amazon.com/AmazonS3/latest/userguide/create-bucket-overview.html) for the CLI to store the artifacts while the analysis is running. The artifacts are deleted after the analysis is completed. The same bucket will be reused for all the repositories that are analyzed in the same account and region (unless specified otherwise by the user). Note that CodeGuru Reviewer expects the S3 bucket name to begin with codeguru-reviewer-. At this time, you can’t use a different naming pattern. However, if you want to use a different bucket name, then you can use the –bucket-name option.\n\nSelect the Permissions tab of your S3 bucket. Update the Block public access and add the following S3 bucket policy.\n\n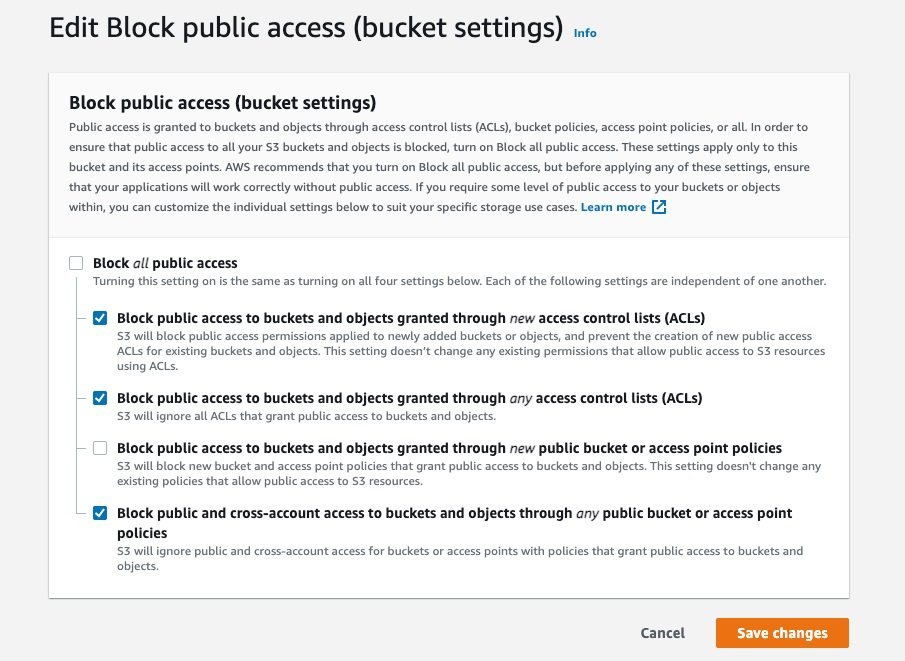\n\nFigure 7: S3 bucket settings\n\n**S3 bucket policy:**\n\nJSON\n```\n{\n \"Version\":\"2012-10-17\",\n \"Statement\":[\n {\n \"Sid\":\"PublicRead\",\n \"Effect\":\"Allow\",\n \"Principal\":\"*\",\n \"Action\":\"s3:GetObject\",\n \"Resource\":\"[Change to ARN for your S3 bucket]/*\"\n }\n ]\n}\n```\nNote that if you must change the bucket’s name, then you can remove the associated S3 bucket in the AWS console under* CodeGuru → CI workflows* and select Disassociate Workflow.\n\n#### **b. Analyzing a single commit**\nThe CLI also lets us specify a specific commit range to analyze. This can lead to faster and more cost-effective scans for the incremental code changes, instead of a full repository scan. For example, if we just want to analyze the last commit, we can run:\n\nBash\n```\naws-codeguru-cli -r ./ -s src/main/java -b build/libs -c HEAD^:HEAD --no-prompt\n```\nHere, we use the -c option to specify that we only want to analyze the commits between *HEAD^* (the previous commit) and HEAD (the current commit). Moreover, we add the –no-prompt option to automatically answer questions by the CLI with yes. This option is useful if we plan to use the CLI in an automated way, such as in our CI/CD workflow.\n\n#### **c. Encrypting artifacts**\nCodeGuru Reviewer lets us use a [customer managed key](customer managed key) to encrypt the content of the S3 bucket that is used to store the source and build artifacts. To achieve this, create a customer owned key in [AWS Key Management Service (AWS KMS)](https://aws.amazon.com/kms/) (see Figure 8).\n\n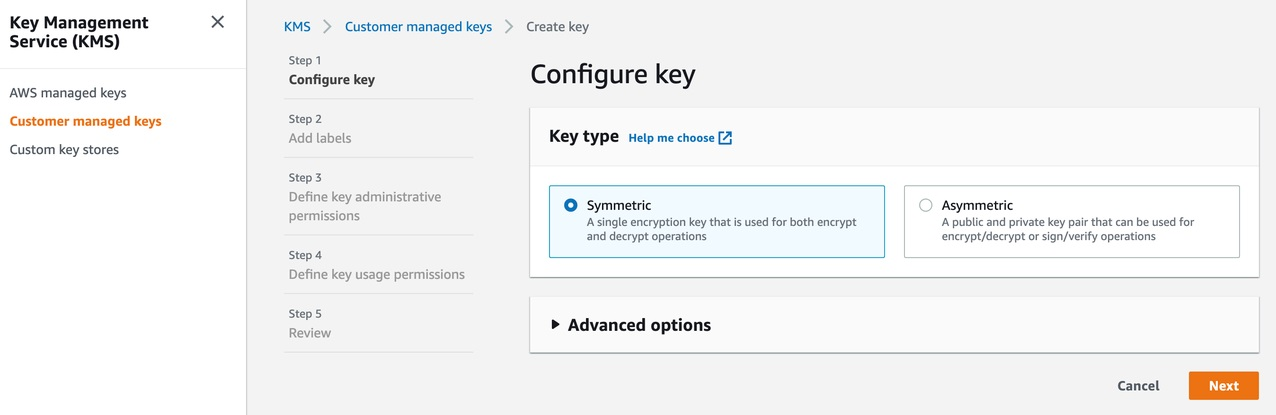\n\nFigure 8: KMS settings\n\nWe must grant CodeGuru Reviewer the permission to decrypt artifacts with this key by adding the following Statement to your Key policy:\n\nJSON\n```\n{\n \"Sid\":\"Allow CodeGuru to use the key to decrypt artifact\",\n \"Effect\":\"Allow\",\n \"Principal\":{\n \"AWS\":\"*\"\n },\n \"Action\":[\n \"kms:Decrypt\",\n \"kms:DescribeKey\"\n ],\n \"Resource\":\"*\",\n \"Condition\":{\n \"StringEquals\":{\n \"kms:ViaService\":\"codeguru-reviewer.amazonaws.com\",\n \"kms:CallerAccount\":[\n \"YOUR AWS ACCOUNT ID\"\n ]\n }\n }\n}\n```\nThen, enable server-side encryption for the S3 bucket that we’re using with CodeGuru Reviewer (Figure 9).\n\n**S3 bucket settings:**\n\n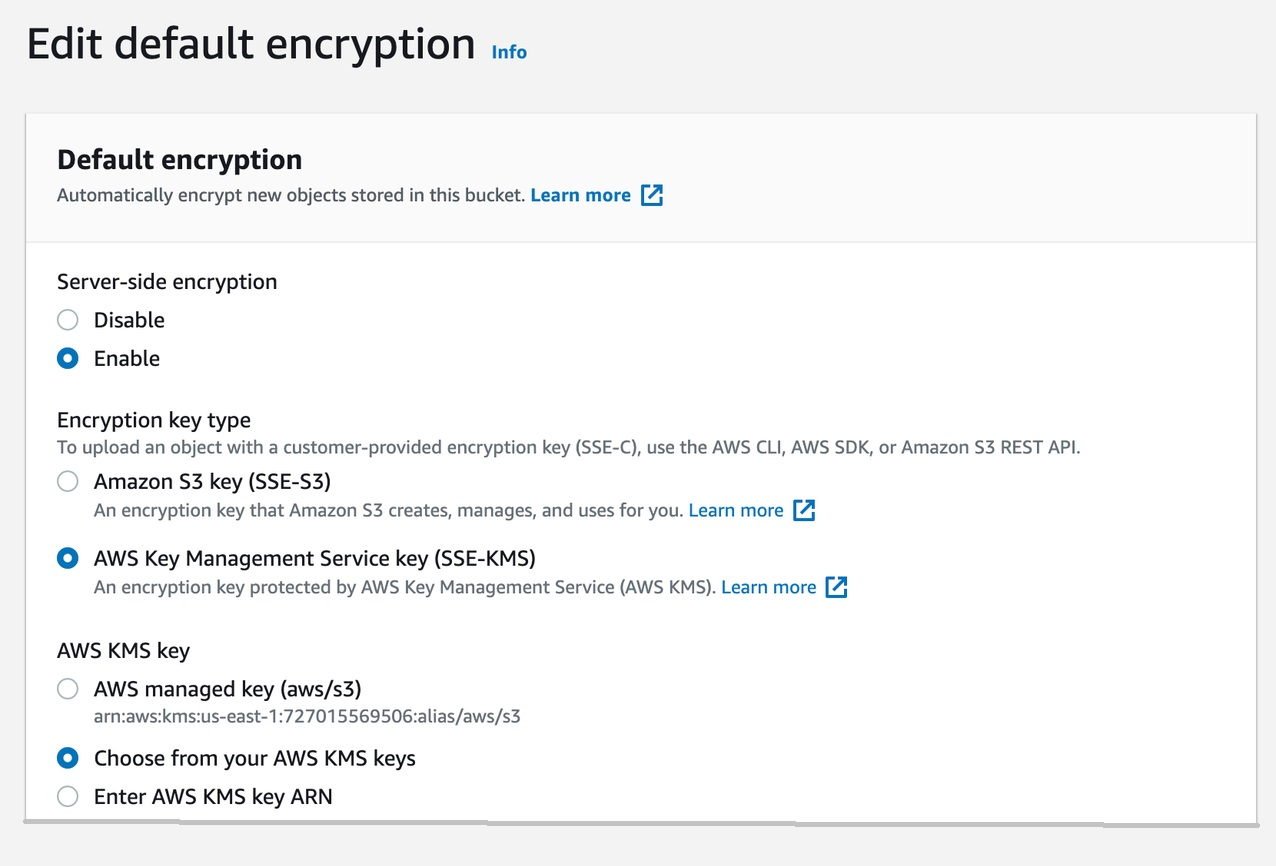\n\nFigure 9: S3 bucket encryption settings\n\nAfter we enable encryption on the bucket, we must delete all the CodeGuru repository associations that use this bucket, and then recreate them by analyzing the repositories while providing the key (as in the following example, Figure 10):\n\n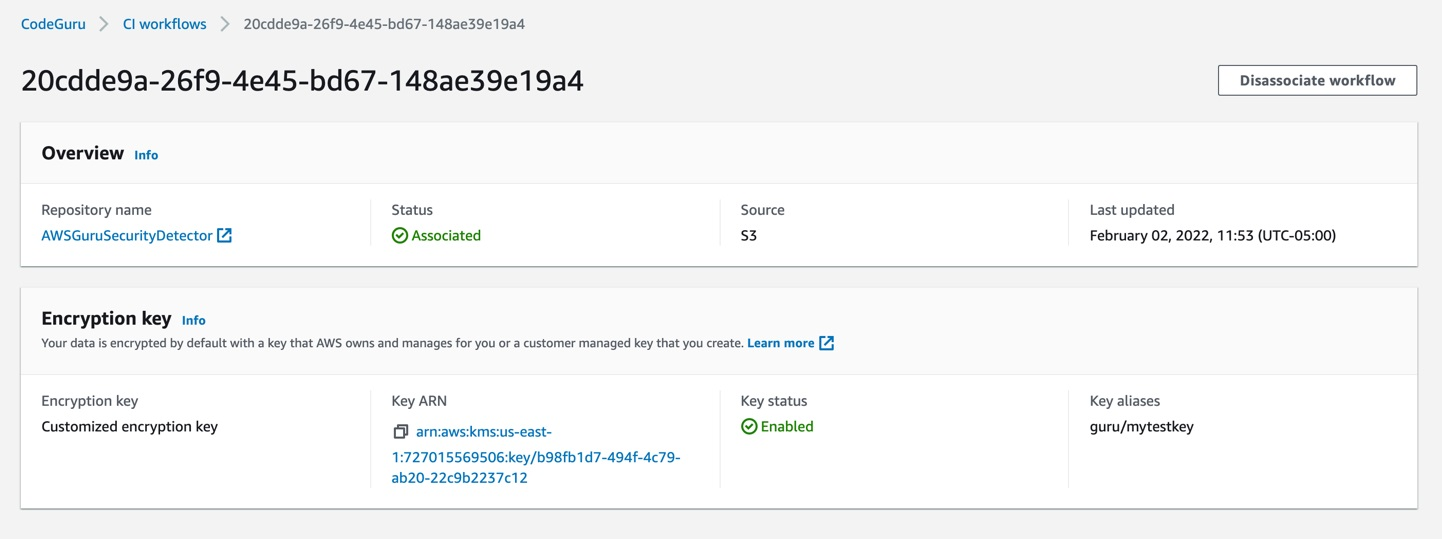\n\nFigure 10: CodeGuru CI Workflow\n\nNote that the first time you check out your repository, it will always trigger a full repository scan. Consider setting the -c option, as this will allow a commit range.\n\n### **Cleaning Up**\nAt this stage, you may choose to delete the resources created while following this blog, to avoid incurring any unwanted costs.\n\n1. [Delete Amazon S3 bucket](https://docs.aws.amazon.com/AmazonS3/latest/userguide/delete-bucket.html).\n2. [Delete AWS KMS key](https://docs.aws.amazon.com/kms/latest/developerguide/deleting-keys.html).\n3. Delete the Jenkins installation, if not required further.\n\n### **Conclusion**\nIn this post, we outlined how you can integrate [Amazon CodeGuru Reviewer CLI](https://github.com/aws/aws-codeguru-cli/) with the Jenkins open-source build automation tool to perform code analysis as part of your code build pipeline and act as a quality gate. We showed you how to create a Jenkins pipeline job and integrate the CodeGuru Reviewer CLI to detect issues in your Java and Python code, as well as access the recommendations for remediating these issues. We presented an example where you can stop the build upon finding critical violations. Furthermore, we discussed how you can specify a commit range to avoid a full repo scan, and how the S3 bucket used by CodeGuru Reviewer to store artifacts can be encrypted using customer managed keys.\n\nThe CodeGuru Reviewer CLI offers you a one-line command to scan any code on your machine and retrieve recommendations. You can run the CLI anywhere where you can run AWS commands. In other words, you can use the CLI to integrate CodeGuru Reviewer into your favourite CI tool, as a pre-commit hook, or anywhere else in your workflow. In turn, you can combine CodeGuru Reviewer with [Dynamic Application Security Testing](https://aws.amazon.com/marketplace/search/results?searchTerms=Dynamic+Application+Security+Testing) (DAST) and [Software Composition Analysis](https://aws.amazon.com/marketplace/search/results?searchTerms=Software+Composition+Analysis) (SCA) tools to achieve a hybrid application security testing method that helps you combine the inside-out and outside-in testing approaches, cross-reference results, and detect vulnerabilities that both exist and are exploitable.\n\nHopefully, you have found this post informative, and the proposed solution useful. If you need helping hands, then [AWS Professional Services](https://aws.amazon.com/professional-services/) can help implement this solution in your enterprise, as well as introduce you to our AWS [DevOps](https://aws.amazon.com/devops/what-is-devops/) services and offerings.\n\n#### **About the Authors**\n\n\n\n**Akash Verma**\nAkash is a Software Development Engineer 2 at Amazon India. He is passionate about writing clean code and building maintainable software. He also enjoys learning modern technologies. Outside of work, Akash loves to travel, interact with new people, and try different cuisines. He also relishes gardening and watching Stand-up comedy.\n\n\n\n**Debashish Chakrabarty**\nDebashish is a Sr. Engagement Manager at AWS Professional Services, India with over 21+ years of experience in various IT roles. At ProServe he leads engagements on Security, App Modernization and Migrations to help ProServe customers accelerate their cloud journey and achieve their business goals. Off work, Debashish has been a Hindi Blogger & Podcaster. He loves binge-watching OTT shows and spending time with family.\n\n\n\n**David Ernst**\nDavid is a Sr. Specialist Solution Architect – DevOps, with 20+ years of experience in designing and implementing software solutions for various industries. David is an automation enthusiast and works with AWS customers to design, deploy, and manage their AWS workloads/architectures.","render":"<p>Watts S. Humphrey, the father of Software Quality, had famously quipped, “Every business is a software business”. Software is indeed integral to any industry. The engineers who create software are also responsible for making sure that the underlying code adheres to industry and organizational standards, are performant, and are absolved of any security vulnerabilities that could make them susceptible to attack.</p>\n<p>Traditionally, security testing has been the forte of a specialized security testing team, who would conduct their tests toward the end of the Software Development lifecycle (SDLC). The adoption of <a href=\"https://aws.amazon.com/blogs/security/tag/devsecops/\" target=\"_blank\">DevSecOps</a> practices meant that security became a shared responsibility between the development and security teams. Now, development teams can, on their own or as advised by their security team, setup and configure various code scanning tools to detect security vulnerabilities much earlier in the software delivery process (aka “<a href=\"https://www.drdobbs.com/shift-left-testing/184404768\" target=\"_blank\">Shift Left</a>”). Meanwhile, the practice of Static code analysis and security application testing (SAST) has become a standard part of the SDLC. Furthermore, it’s imperative that the development teams expect SAST tools that are easy to set-up, seamlessly fit into their DevOps infrastructure, and can be configured without requiring assistance from security or DevOps experts.</p>\n<p>In this post, we’ll demonstrate how you can leverage <a href=\"https://aws.amazon.com/codeguru/\" target=\"_blank\">Amazon CodeGuru</a> Reviewer Command Line Interface (CLI) to integrate CodeGuru Reviewer into your Jenkins Continuous Integration & Continuous Delivery (CI/CD) pipeline. Note that the solution isn’t limited to Jenkins, and it would be equally useful with any other build automation tool. Moreover, it can be integrated at any stage of your SDLC as part of the White-box testing. For example, you can integrate the <a href=\"https://docs.aws.amazon.com/cli/latest/reference/codeguru-reviewer/index.html\" target=\"_blank\">CodeGuru Reviewer CLI</a> as part of your software development process, as well as run it on your dev machine before committing the code.</p>\n<p>Launched in 2020, CodeGuru Reviewer utilizes machine learning (ML) and automated reasoning to identify security vulnerabilities, inefficient uses of AWS APIs and SDKs, as well as other common coding errors. CodeGuru Reviewer employs a growing set of <a href=\"https://docs.aws.amazon.com/codeguru/detector-library/\" target=\"_blank\">detectors</a> for Java and Python to provide recommendations via the <a href=\"https://aws.amazon.com/console/\" target=\"_blank\">AWS Console</a>. Customers that leverage the CodeGuru Reviewer CLI within a CI/CD pipeline also receive recommendations in a machine-readable JSON format, as well as HTML.</p>\n<p>CodeGuru Reviewer offers native integration with Source Code Management (SCM) systems, such as GitHub, BitBucket, and <a href=\"https://aws.amazon.com/codecommit/\" target=\"_blank\">AWS CodeCommit</a>. However, it can be used with any SCM via its CLI. The CodeGuru Reviewer CLI is a shim layer on top of the <a href=\"https://aws.amazon.com/cli/\" target=\"_blank\">AWS Command Line Interface (AWS CLI)</a> that simplifies the interaction with the tool by handling the uploading of artifacts, triggering of the analysis, and fetching of the results, all in a single command.</p>\n<p>Many customers, including Mastercard, are benefiting from this new CodeGuru Reviewer CLI.</p>\n<p>“During one of our technical retrospectives, we noticed the need to integrate Amazon CodeGuru recommendations in our build pipelines hosted on Jenkins. Not all our developers can run or check CodeGuru recommendations through the AWS console. Incorporating CodeGuru CLI in our build pipelines acts as an important quality gate and ensures that our developers can immediately fix critical issues.”<br />\n<em>Claudio Frattari, Lead DevOps at Mastercard</em></p>\n<h3><a id=\"Solution_overview_15\"></a><strong>Solution overview</strong></h3>\n<p>The application deployment workflow starts by placing the application code on a GitHub SCM. To automate the scenario, we have added GitHub to the Jenkins project under the “Source Code” section. We chose the GitHub option, which would clone the chosen GitHub repository in the Jenkins local workspace directory.</p>\n<p>In the build stage of the pipeline (see Figure 1), we configure the appropriate build tool to perform the code build and security analysis. In this example, we will be using <a href=\"https://maven.apache.org/\" target=\"_blank\">Maven</a> as the build tool.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/968cf2587e9e45609984a421eafad044_image.png\" alt=\"image.png\" /></p>\n<p>Figure 1: Jenkins pipeline with Amazon CodeGuru Reviewer</p>\n<p>In the post-build stage, we configure the CodeGuru Reviewer CLI to generate the recommendations based on the review.</p>\n<p>Lastly, in the concluding stage of the pipeline, we’ll be analyzing the JSON results using <a href=\"https://stedolan.github.io/jq/!%5Bimage.png%5D(https://dev-media.amazoncloud.cn/d4f645be94934df2bb756290ff9b1c73_image.png)\" target=\"_blank\">jq</a> – a lightweight and flexible command-line JSON processor, and then failing the Jenkins job if we encounter observations that are of a “Critical” severity.</p>\n<p>Jenkins will trigger the “CodeGuru Reviewer” (see Figure 1) based review process in the post-build stage, i.e., after the build finishes. Furthermore, you can configure other stages, such as automated testing or deployment, after this stage. Additionally, passing the location of the build artifacts to the CLI lets CodeGuru Reviewer perform a more in-depth security analysis. Build artifacts are either directories containing jar files (e.g., <em>build/lib for Gradle or /target</em> for Maven) or directories containing class hierarchies (e.g., <em>build/classes/java/main</em> for Gradle).</p>\n<h3><a id=\"Walkthrough_30\"></a><strong>Walkthrough</strong></h3>\n<p>Now that we have an overview of the workflow, let’s dive deep and walk you through the following steps in detail:</p>\n<ol>\n<li>Installing the CodeGuru Reviewer CLI</li>\n<li>Creating a Jenkins pipeline job</li>\n<li>Reviewing the CodeGuru Reviewer recommendations</li>\n<li>Configuring CodeGuru Reviewer CLI’s additional options</li>\n</ol>\n<h3><a id=\"1_Installing_the_CodeGuru_CLI_Wrapper_38\"></a><strong>1. Installing the CodeGuru CLI Wrapper</strong></h3>\n<h4><a id=\"a_Prerequisites_39\"></a><strong>a. Prerequisites</strong></h4>\n<p>To run the CLI, we must have Git, Java, Maven, and the AWS CLI installed. Verify that they’re installed on our machine by running the following commands:</p>\n<p>Bash</p>\n<pre><code class=\"lang-\">java -version \nmvn --version \naws --version \ngit –-version\n</code></pre>\n<p>If they aren’t installed, then download and install Java <a href=\"https://aws.amazon.com/corretto/\" target=\"_blank\">here</a> (Amazon Corretto is a no-cost, multiplatform, production-ready distribution of the Open Java Development Kit), Maven from <a href=\"https://maven.apache.org/download.cgi\" target=\"_blank\">here</a>, and Git from <a href=\"https://git-scm.com/downloads\" target=\"_blank\">here</a>. Instructions for installing AWS CLI are available <a href=\"https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html\" target=\"_blank\">here</a>.</p>\n<p>We would need to create an <a href=\"https://aws.amazon.com/s3/\" target=\"_blank\">Amazon Simple Storage Service (Amazon S3) </a>bucket with the prefix codeguru-reviewer-. Note that the bucket name must begin with the mentioned prefix, since we have used the name pattern in the following <a href=\"https://aws.amazon.com/iam/\" target=\"_blank\">AWS Identity and Access Management (IAM)</a> permissions, and CodeGuru Reviewer expects buckets to begin with this prefix. Refer to the following section 4(a) “Specifying S3 bucket name” for more details.</p>\n<p>Furthermore, we’ll need working credentials on our machine to interact with our <a href=\"https://aws.amazon.com/premiumsupport/knowledge-center/create-and-activate-aws-account/\" target=\"_blank\">AWS account</a>. Learn more about setting up credentials for AWS <a href=\"https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-configure.html\" target=\"_blank\">here</a>. You can find the minimal permissions to run the CodeGuru Reviewer CLI as follows.</p>\n<h4><a id=\"b_Required_Permissions_56\"></a><strong>b. Required Permissions</strong></h4>\n<p>To use the CodeGuru Reviewer CLI, we need at least the following AWS IAM permissions, attached to an AWS IAM User or an AWS IAM role:</p>\n<p>JSON</p>\n<pre><code class=\"lang-\">{\n "Version": "2012-10-17",\n "Statement": [\n {\n "Action": [\n "codeguru-reviewer:ListRepositoryAssociations",\n "codeguru-reviewer:AssociateRepository",\n "codeguru-reviewer:DescribeRepositoryAssociation",\n "codeguru-reviewer:CreateCodeReview",\n "codeguru-reviewer:DescribeCodeReview",\n "codeguru-reviewer:ListRecommendations",\n "iam:CreateServiceLinkedRole"\n ],\n "Resource": "*",\n "Effect": "Allow"\n },\n {\n "Action": [\n "s3:CreateBucket",\n "s3:GetBucket*",\n "s3:List*",\n "s3:GetObject",\n "s3:PutObject",\n "s3:DeleteObject"\n ],\n "Resource": [\n "arn:aws:s3:::codeguru-reviewer-*",\n "arn:aws:s3:::codeguru-reviewer-*/*"\n ],\n "Effect": "Allow"\n }\n ]\n}\n</code></pre>\n<h4><a id=\"c__CLI_installation_95\"></a><strong>c. CLI installation</strong></h4>\n<p>Please download the latest version of the CodeGuru Reviewer CLI available at GitHub. Then, run the following commands in sequence:</p>\n<p>Bash</p>\n<pre><code class=\"lang-\">curl -OL https://github.com/aws/aws-codeguru-cli/releases/download/0.0.1/aws-codeguru-cli.zip\nunzip aws-codeguru-cli.zip\nexport PATH=$PATH:./aws-codeguru-cli/bin\n</code></pre>\n<h4><a id=\"d_Using_the_CLI_104\"></a><strong>d. Using the CLI</strong></h4>\n<p>The CodeGuru Reviewer CLI only has one required parameter –root-dir (or just -r) to specify to the local directory that should be analyzed. Furthermore, the –src option can be used to specify one or more files in this directory that contain the source code that should be analyzed. In turn, for Java applications, the –build option can be used to specify one or more build directories.</p>\n<p>For a demonstration, we’ll analyze the demo application. This will make sure that we’re all set for when we leverage the CLI in Jenkins. To proceed, first we download and install the sample application, as follows:</p>\n<p>Bash</p>\n<pre><code class=\"lang-\">git clone https://github.com/aws-samples/amazon-codeguru-reviewer-sample-app\ncd amazon-codeguru-reviewer-sample-app\nmvn clean compile\n</code></pre>\n<p>Now that we have built our demo application, we can use the aws-codeguru-cli CLI command that we added to the path to trigger the code scan:</p>\n<p>Bash</p>\n<pre><code class=\"lang-\">aws-codeguru-cli --root-dir ./ --build target/classes --src src --output ./output\n</code></pre>\n<p>For additional assistance on the CLI command, reference the readme <a href=\"https://github.com/aws/aws-codeguru-cli\" target=\"_blank\">here</a>.</p>\n<h3><a id=\"2__Creating_a_Jenkins_Pipeline_job_122\"></a><strong>2. Creating a Jenkins Pipeline job</strong></h3>\n<p>CodeGuru Reviewer can be integrated in a Jenkins Pipeline as well as a Freestyle project. In this example, we’re leveraging a Pipeline.</p>\n<h4><a id=\"a_Pipeline_Job_Configuration_125\"></a><strong>a. Pipeline Job Configuration</strong></h4>\n<ol>\n<li>Log in to Jenkins, choose “New Item”, then select “Pipeline” option.</li>\n<li>Enter a name for the project (for example, “CodeGuruPipeline”), and choose OK.</li>\n</ol>\n<p><img src=\"https://dev-media.amazoncloud.cn/64ee84f3a56c4dc8b20f4aa3e0810b3a_image.png\" alt=\"image.png\" /></p>\n<p>Figure 2: Creating a new Jenkins pipeline</p>\n<ol start=\"3\">\n<li>On the “Project configuration” page, scroll down to the bottom and find your pipeline. In the pipeline script, paste the following script (or use your own Jenkinsfile). The following example is a valid Jenkinsfile to integrate CodeGuru Reviewer with a project built using Maven.</li>\n</ol>\n<pre><code class=\"lang-\">pipeline {\n agent any\n stages {\n stage('Build') {\n steps {\n // Get code from a GitHub repository\n git clone https://github.com/aws-samples/amazon-codeguru-reviewer-java-detectors.git\n\n // Run Maven on a Unix agent\n sh "mvn clean compile"\n\n // To run Maven on a Windows agent, use following\n // bat "mvn -Dmaven.test.failure.ignore=true clean package"\n }\n }\n stage('CodeGuru Reviewer') {\n steps{\n sh 'ls -lsa *'\n sh 'pwd'\n // Here we’re setting an absolute path, but we can \n // also use JENKINS environment variables\n sh '''\n export BASE=/var/jenkins_home/workspace/CodeGuruPipeline/amazon-codeguru-reviewer-java-detectors\n export SRC=${BASE}/src\n export OUTPUT = ./output\n /home/codeguru/aws-codeguru-cli/bin/aws-codeguru-cli --root-dir $BASE --build $BASE/target/classes --src $SRC --output $OUTPUT -c $GIT_PREVIOUS_COMMIT:$GIT_COMMIT --no-prompt\n '''\n }\n } \n stage('Checking findings'){\n steps{\n // In this example we are stopping our pipline on \n // detecting Critical findings. We are using jq \n // to count occurrences of Critical severity \n sh '''\n CNT = $(cat ./output/recommendations.json |jq '.[] | select(.severity=="Critical")|.severity' | wc -l)'\n if (( $CNT > 0 )); then\n echo "Critical findings discovered. Failing."\n exit 1\n fi\n '''\n }\n }\n }\n}\n</code></pre>\n<ol start=\"4\">\n<li>Save the configuration and select “Build now” on the side bar to trigger the build process (see Figure 3).</li>\n</ol>\n<p><img src=\"https://dev-media.amazoncloud.cn/4204ff66ee344366819f7f0f9b48efe9_image.png\" alt=\"image.png\" /></p>\n<p>Figure 3: Jenkins pipeline in triggered state</p>\n<h3><a id=\"3_Reviewing_the_CodeGuru_Reviewer_recommendations_187\"></a><strong>3. Reviewing the CodeGuru Reviewer recommendations</strong></h3>\n<p>Once the build process is finished, you can view the review results from CodeGuru Reviewer by selecting the Jenkins build history for the most recent build job. Then, browse to Workspace output. The output is available in JSON and HTML formats (Figure 4).</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/1768c8fb5717468e9131cf2a0fd67549_image.png\" alt=\"image.png\" /></p>\n<p>Figure 4: CodeGuru CLI Output</p>\n<p>Snippets from the HTML and JSON reports are displayed in Figure 5 and 6 respectively.</p>\n<p>In this example, our pipeline analyzes the JSON results with jq based on severity equal to critical and failing the job if there are any critical findings. Note that this output path is set with the –output option. For instance, the pipeline will fail on noticing the “critical” finding at Line 67 of the EventHandler.java class (Figure 5), flagged due to use of an insecure code. Till the time the code is remediated, the pipeline would prevent the code deployment. The vulnerability could have gone to production undetected, in absence of the tool.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/627189f5871e440f8cd49581c7642ef4_image.png\" alt=\"image.png\" /></p>\n<p>Figure 5: CodeGuru HTML Report</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/71ee5e4ed82b491bb03d60369e1a4a4b_image.png\" alt=\"image.png\" /></p>\n<p>Figure 6: CodeGuru JSON recommendations</p>\n<h3><a id=\"4Configuring_CodeGuru_Reviewer_CLIs_additional_options_207\"></a><strong>4.Configuring CodeGuru Reviewer CLI’s additional options</strong></h3>\n<h4><a id=\"a__Specifying_Amazon_S3_bucket_name_and_policy_208\"></a><strong>a. Specifying Amazon S3 bucket name and policy</strong></h4>\n<p>CodeGuru Reviewer needs one <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/create-bucket-overview.html\" target=\"_blank\">Amazon S3 bucket</a> for the CLI to store the artifacts while the analysis is running. The artifacts are deleted after the analysis is completed. The same bucket will be reused for all the repositories that are analyzed in the same account and region (unless specified otherwise by the user). Note that CodeGuru Reviewer expects the S3 bucket name to begin with codeguru-reviewer-. At this time, you can’t use a different naming pattern. However, if you want to use a different bucket name, then you can use the –bucket-name option.</p>\n<p>Select the Permissions tab of your S3 bucket. Update the Block public access and add the following S3 bucket policy.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/a2d3ca4340d44cb4bf7d2548b4b1e0f0_image.png\" alt=\"image.png\" /></p>\n<p>Figure 7: S3 bucket settings</p>\n<p><strong>S3 bucket policy:</strong></p>\n<p>JSON</p>\n<pre><code class=\"lang-\">{\n "Version":"2012-10-17",\n "Statement":[\n {\n "Sid":"PublicRead",\n "Effect":"Allow",\n "Principal":"*",\n "Action":"s3:GetObject",\n "Resource":"[Change to ARN for your S3 bucket]/*"\n }\n ]\n}\n</code></pre>\n<p>Note that if you must change the bucket’s name, then you can remove the associated S3 bucket in the AWS console under* CodeGuru → CI workflows* and select Disassociate Workflow.</p>\n<h4><a id=\"b__Analyzing_a_single_commit_236\"></a><strong>b. Analyzing a single commit</strong></h4>\n<p>The CLI also lets us specify a specific commit range to analyze. This can lead to faster and more cost-effective scans for the incremental code changes, instead of a full repository scan. For example, if we just want to analyze the last commit, we can run:</p>\n<p>Bash</p>\n<pre><code class=\"lang-\">aws-codeguru-cli -r ./ -s src/main/java -b build/libs -c HEAD^:HEAD --no-prompt\n</code></pre>\n<p>Here, we use the -c option to specify that we only want to analyze the commits between <em>HEAD^</em> (the previous commit) and HEAD (the current commit). Moreover, we add the –no-prompt option to automatically answer questions by the CLI with yes. This option is useful if we plan to use the CLI in an automated way, such as in our CI/CD workflow.</p>\n<h4><a id=\"c__Encrypting_artifacts_245\"></a><strong>c. Encrypting artifacts</strong></h4>\n<p>CodeGuru Reviewer lets us use a [customer managed key](customer managed key) to encrypt the content of the S3 bucket that is used to store the source and build artifacts. To achieve this, create a customer owned key in <a href=\"https://aws.amazon.com/kms/\" target=\"_blank\">AWS Key Management Service (AWS KMS)</a> (see Figure 8).</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/d6dc23b164324c01901c314d2b8ceae5_image.png\" alt=\"image.png\" /></p>\n<p>Figure 8: KMS settings</p>\n<p>We must grant CodeGuru Reviewer the permission to decrypt artifacts with this key by adding the following Statement to your Key policy:</p>\n<p>JSON</p>\n<pre><code class=\"lang-\">{\n "Sid":"Allow CodeGuru to use the key to decrypt artifact",\n "Effect":"Allow",\n "Principal":{\n "AWS":"*"\n },\n "Action":[\n "kms:Decrypt",\n "kms:DescribeKey"\n ],\n "Resource":"*",\n "Condition":{\n "StringEquals":{\n "kms:ViaService":"codeguru-reviewer.amazonaws.com",\n "kms:CallerAccount":[\n "YOUR AWS ACCOUNT ID"\n ]\n }\n }\n}\n</code></pre>\n<p>Then, enable server-side encryption for the S3 bucket that we’re using with CodeGuru Reviewer (Figure 9).</p>\n<p><strong>S3 bucket settings:</strong></p>\n<p><img src=\"https://dev-media.amazoncloud.cn/1e271f89dea346dab9d59a551edd72bc_image.png\" alt=\"image.png\" /></p>\n<p>Figure 9: S3 bucket encryption settings</p>\n<p>After we enable encryption on the bucket, we must delete all the CodeGuru repository associations that use this bucket, and then recreate them by analyzing the repositories while providing the key (as in the following example, Figure 10):</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/e59e655ffd3b46018d3b4f35f5354bd3_image.png\" alt=\"image.png\" /></p>\n<p>Figure 10: CodeGuru CI Workflow</p>\n<p>Note that the first time you check out your repository, it will always trigger a full repository scan. Consider setting the -c option, as this will allow a commit range.</p>\n<h3><a id=\"Cleaning_Up_293\"></a><strong>Cleaning Up</strong></h3>\n<p>At this stage, you may choose to delete the resources created while following this blog, to avoid incurring any unwanted costs.</p>\n<ol>\n<li><a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/delete-bucket.html\" target=\"_blank\">Delete Amazon S3 bucket</a>.</li>\n<li><a href=\"https://docs.aws.amazon.com/kms/latest/developerguide/deleting-keys.html\" target=\"_blank\">Delete AWS KMS key</a>.</li>\n<li>Delete the Jenkins installation, if not required further.</li>\n</ol>\n<h3><a id=\"Conclusion_300\"></a><strong>Conclusion</strong></h3>\n<p>In this post, we outlined how you can integrate <a href=\"https://github.com/aws/aws-codeguru-cli/\" target=\"_blank\">Amazon CodeGuru Reviewer CLI</a> with the Jenkins open-source build automation tool to perform code analysis as part of your code build pipeline and act as a quality gate. We showed you how to create a Jenkins pipeline job and integrate the CodeGuru Reviewer CLI to detect issues in your Java and Python code, as well as access the recommendations for remediating these issues. We presented an example where you can stop the build upon finding critical violations. Furthermore, we discussed how you can specify a commit range to avoid a full repo scan, and how the S3 bucket used by CodeGuru Reviewer to store artifacts can be encrypted using customer managed keys.</p>\n<p>The CodeGuru Reviewer CLI offers you a one-line command to scan any code on your machine and retrieve recommendations. You can run the CLI anywhere where you can run AWS commands. In other words, you can use the CLI to integrate CodeGuru Reviewer into your favourite CI tool, as a pre-commit hook, or anywhere else in your workflow. In turn, you can combine CodeGuru Reviewer with <a href=\"https://aws.amazon.com/marketplace/search/results?searchTerms=Dynamic+Application+Security+Testing\" target=\"_blank\">Dynamic Application Security Testing</a> (DAST) and <a href=\"https://aws.amazon.com/marketplace/search/results?searchTerms=Software+Composition+Analysis\" target=\"_blank\">Software Composition Analysis</a> (SCA) tools to achieve a hybrid application security testing method that helps you combine the inside-out and outside-in testing approaches, cross-reference results, and detect vulnerabilities that both exist and are exploitable.</p>\n<p>Hopefully, you have found this post informative, and the proposed solution useful. If you need helping hands, then <a href=\"https://aws.amazon.com/professional-services/\" target=\"_blank\">AWS Professional Services</a> can help implement this solution in your enterprise, as well as introduce you to our AWS <a href=\"https://aws.amazon.com/devops/what-is-devops/\" target=\"_blank\">DevOps</a> services and offerings.</p>\n<h4><a id=\"About_the_Authors_307\"></a><strong>About the Authors</strong></h4>\n<p><img src=\"https://dev-media.amazoncloud.cn/6bb35aa21fdd4f949474ce710d6d14fa_image.png\" alt=\"image.png\" /></p>\n<p><strong>Akash Verma</strong><br />\nAkash is a Software Development Engineer 2 at Amazon India. He is passionate about writing clean code and building maintainable software. He also enjoys learning modern technologies. Outside of work, Akash loves to travel, interact with new people, and try different cuisines. He also relishes gardening and watching Stand-up comedy.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/5c64eeada14045b3b6f856caf3f4d8c5_image.png\" alt=\"image.png\" /></p>\n<p><strong>Debashish Chakrabarty</strong><br />\nDebashish is a Sr. Engagement Manager at AWS Professional Services, India with over 21+ years of experience in various IT roles. At ProServe he leads engagements on Security, App Modernization and Migrations to help ProServe customers accelerate their cloud journey and achieve their business goals. Off work, Debashish has been a Hindi Blogger & Podcaster. He loves binge-watching OTT shows and spending time with family.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/de022c9eec024e9694e22121ae5febb6_image.png\" alt=\"image.png\" /></p>\n<p><strong>David Ernst</strong><br />\nDavid is a Sr. Specialist Solution Architect – DevOps, with 20+ years of experience in designing and implementing software solutions for various industries. David is an automation enthusiast and works with AWS customers to design, deploy, and manage their AWS workloads/architectures.</p>\n"}
Automating detection of security vulnerabilities and bugs in CI/CD pipelines using Amazon CodeGuru Reviewer CLI
海外精选
海外精选的内容汇集了全球优质的亚马逊云科技相关技术内容。同时,内容中提到的“AWS”
是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。

 0
0 0
0亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
目录
亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
亚马逊云科技解决方案
基于行业客户应用场景及技术领域的解决方案
联系专家
0
目录
 分享
分享 点赞
点赞 收藏
收藏 目录
目录立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
