{"value":"[Amazon OpenSearch Service](https://aws.amazon.com/opensearch-service/) is a fully managed, distributed, open search, and analytics service that is powered by the Apache Lucene search library. OpenSearch Service is derived from Elasticsearch 7.10.2, and is used for real-time application monitoring, log analytics, and website search. It’s ideal for use cases that require fast access and response for large volumes of data. OpenSearch Dashboards is derived from Kibana 7.10.2, and used for visual data exploration. With Security Assertion Markup Language (SAML)-based federation for OpenSearch Service, OpenSearch Dashboards lets you use your existing identity provider (IdP) like Auth0. You can use Auth0 to provide single sign-on (SSO) for OpenSearch Dashboards on OpenSearch Service domains. It also gives you fine-grained access control, and the ability to search your data and build visualizations. OpenSearch Service supports providers that use the SAML 2.0 standard, such as Auth0, Okta, Keycloak, Active Directory Federation Services (AD FS), and Ping Identity (PingID).\n\nIn this post, we provide step-by-step guidance to show you how to set up a trial Auth0 account. We’ll demonstrate how to build users and groups within your organization’s directory, and enable SP-initiated single sign-on (SSO) into OpenSearch Dashboards.\n\nTo use this feature, you must enable fine-grained access control. Rather than authenticating through [Amazon Cognito](https://aws.amazon.com/cognito/) or an internal user database, SAML authentication for OpenSearch Dashboards lets you use third-party identity providers to log in to the OpenSearch Dashboards. SAML authentication for OpenSearch Dashboards is only for accessing the OpenSearch Dashboards through a web browser. Your SAML credentials do not let you make direct HTTP requests to OpenSearch Service or OpenSearch Dashboards APIs.\n\n[Auth0](http://auth0.com/) is an [Amazon Web Services Competency Partner](https://auth0.com/partners/aws) and popular Identity-as-a-Service (IDaaS) solution. It supports both service provider (SP)-initiated and identity provider (IdP)-initiated SSO. For SP-initiated SSO, when you sign into the OpenSearch Dashboards login page it sends an authorization request to Auth0. Once it authenticates your identity, you are redirected to OpenSearch Dashboards. In IdP-initiated SSO, you log in to the Auth0 SSO page, and choose OpenSearch Dashboards to open the application.\n#### **Overview of AuthO SAML authenticated solution**\nFigure 1 depicts a sample architecture of a generic, integrated solution between Auth0 and OpenSearch Dashboards over SAML authentication.\n\n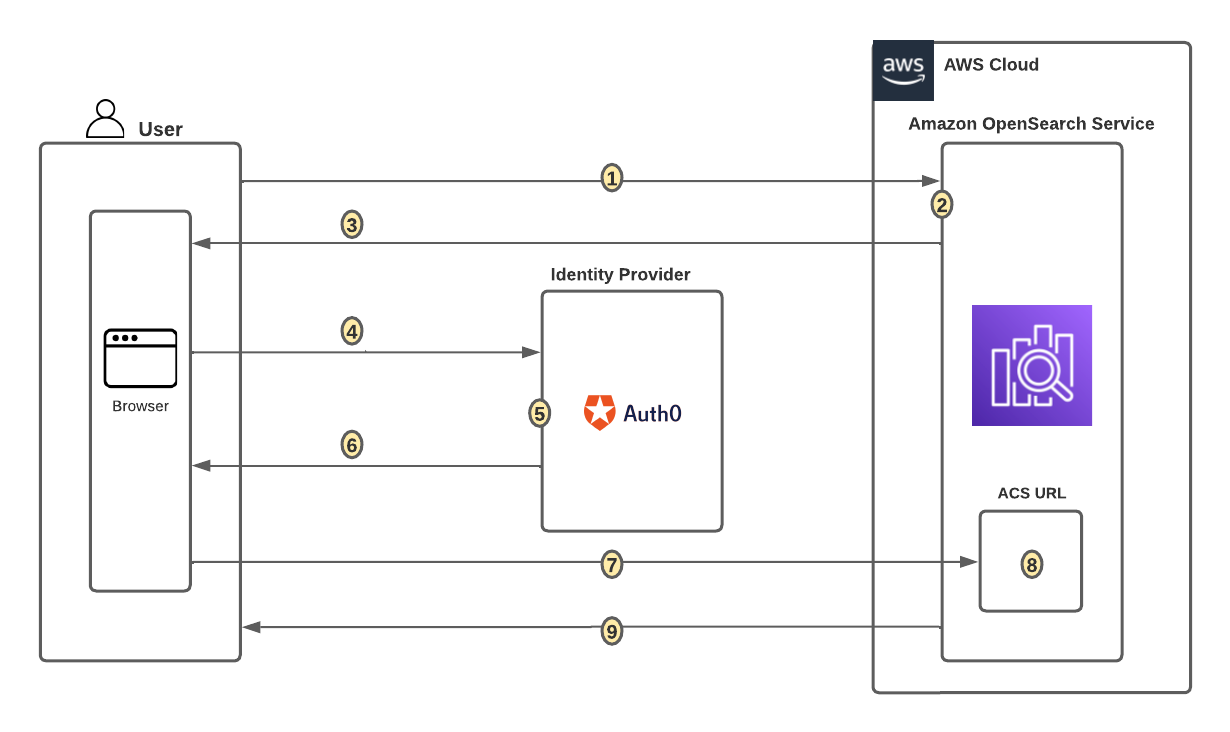\n\nFigure 1. A high-level view of a SAML transaction between Amazon OpenSearch Service and Auth0\n\nThe sign-in flow is as follows:\n\n1. User opens browser window and navigates to OpenSearch Dashboards\n2. OpenSearch Service generates SAML authentication request\n3. OpenSearch Service redirects request back to browser\n4. Browser redirects to Auth0 URL\n5. Auth0 parses SAML request, authenticates user, and generates SAML response\n6. Auth0 returns encoded SAML response to browser\n7. Browser sends SAML response back to OpenSearch Service Assertion Consumer Service (ACS) URL\n8. ACS verifies SAML response\n9. User logs into OpenSearch Service domain\n#### **Prerequisites**\nFor this walkthrough, you should have the following prerequisites:\n1. An [Amazon Web Services account](https://signin.aws.amazon.com/signin?redirect_uri=https%3A%2F%2Fportal.aws.amazon.com%2Fbilling%2Fsignup%2Fresume&client_id=signup)\n2. A virtual private cloud (VPC) based OpenSearch Service domain with fine-grained access control enabled\n3. An Auth0 account with user and a group\n4. A browser with network connectivity to Auth0, OpenSearch Service domain, and OpenSearch Dashboards\n\nThe steps in this post are structured into the following sections:\n1. Identity provider (Auth0) setup\n2. Prepare OpenSearch Service for SAML configuration\n3. Identity provider (Auth0) SAML configuration\n4. Finish OpenSearch Service for SAML configuration\n5. Validation\n6. Cleanup\n#### **Identity provider (Auth0) setup**\n**Step 1: Sign up for an Auth0 account**\n- Sign up for an [ Auth0 account](https://auth0.com/signup), then click on the **Sign up** button to complete your account setup.\n- If you already have an account with Auth0, [log in](https://auth0.com/docs/authenticate/login) to your Auth0 account.\n\n**Step 2: Create Groups in Auth0**\n- Choose **User Management** in the left menu and click **Users**, then click on the **+Create User** button.\n- Provide an email, password, and connection to your users. Click on the **Create** button to create your user.\n- Add more users to your Auth0 account.\n\n**Step 3: Install Auth0 Extension to create a group and assign users to the group**\n- Click on Extensions in the left menu and search for “**Auth0 Authorization**”. Click on **Auth0 Authorization** to install the extension, shown in Figure 2.\n\n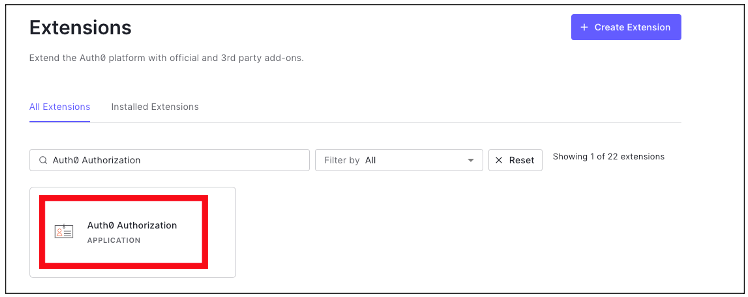\n\nFigure 2. Installing Auth0 Authorization extension\n\n- Use all default options and click on the **Install** button to install the extension.\n- Click on the **Auth0 Authorization** extension and choose the **Accept** button to provide access to your Auth0 account.\n- The **Auth0 Authorization** extension must be configured. Click on **Go to Configuration** (Figure 3).\n\n\nFigure 3. Configuring the Auth0 Authorization extension\n\n- Rotate your API keys and check Groups, Roles, and Permissions to provide authorization to the extension and then click on PUBLISH RULE to complete the configuration, see Figure 4.\n\n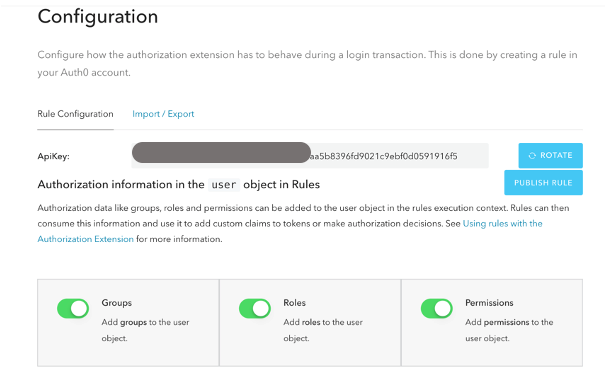\n\nFigure 4. Providing the permissions to Auth0 Authorization extension\n\n**Step 4: Create a group in Auth0**\n- Choose **Groups** from the left menu and click on the **Create your first Group** button. For this example, we will create a group called opensearch for OpenSearch Dashboards access.\n- Add your users to opensearch by clicking on **ADD MEMBERS BUTTON**, then click on the **CONFIRM** button to complete your group assignment (Figure 5).\n\n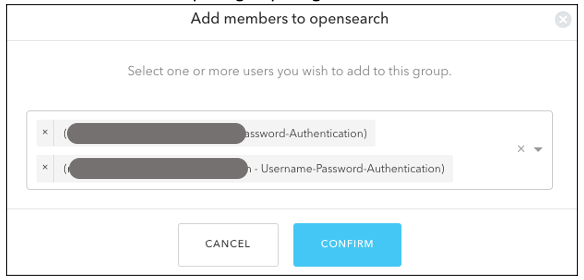\n\nFigure 5. Adding users to Auth0 Group\n\n **Step 5: Create an Auth0 Application**\n\nChoose **Applications** from the left menu. Click on the **+Create Application** button.\nFor this example, we are creating an application called “opensearch”.\nSelect Single Page Web Applications, then click on the **CREATE** button to proceed.\nClick on the **Addons** tab on the application Kibana (Figure 6).\n\n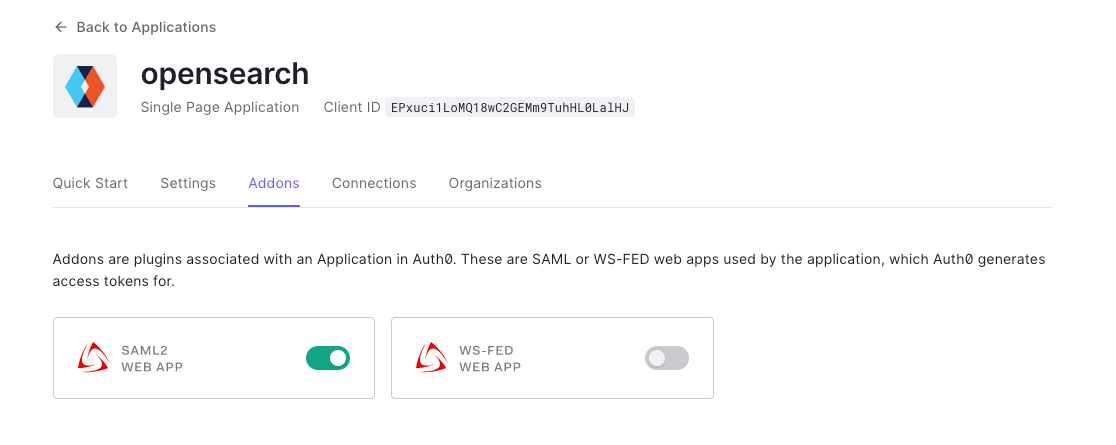\n\nFigure 6. Creating an Auth0 SAML application\n\n- Click on the SAML2 WEB APP, then select settings to provide SAML URLs from OpenSearch Service. We will configure these details after preparing the OpenSearch Service cluster for SAML.\n#### **Prepare OpenSearch Service for SAML configuration**\nOnce the OpenSearch Service domain is up and running, we can proceed with configuration.\n\n- Under Actions, choose Edit security configuration (Figure 7).\n\t\n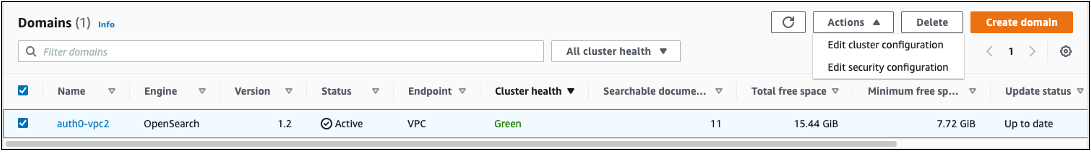\n\nFigure 7. Enabling Amazon OpenSearch Service security configuration for SAML\n\n- Under SAML authentication for OpenSearch Dashboards/Kibana, select the **Enable SAML** authentication check box (Figure 8). When we enable SAML, it will create different URLs required for configuring SAML with your identity provider.\n\n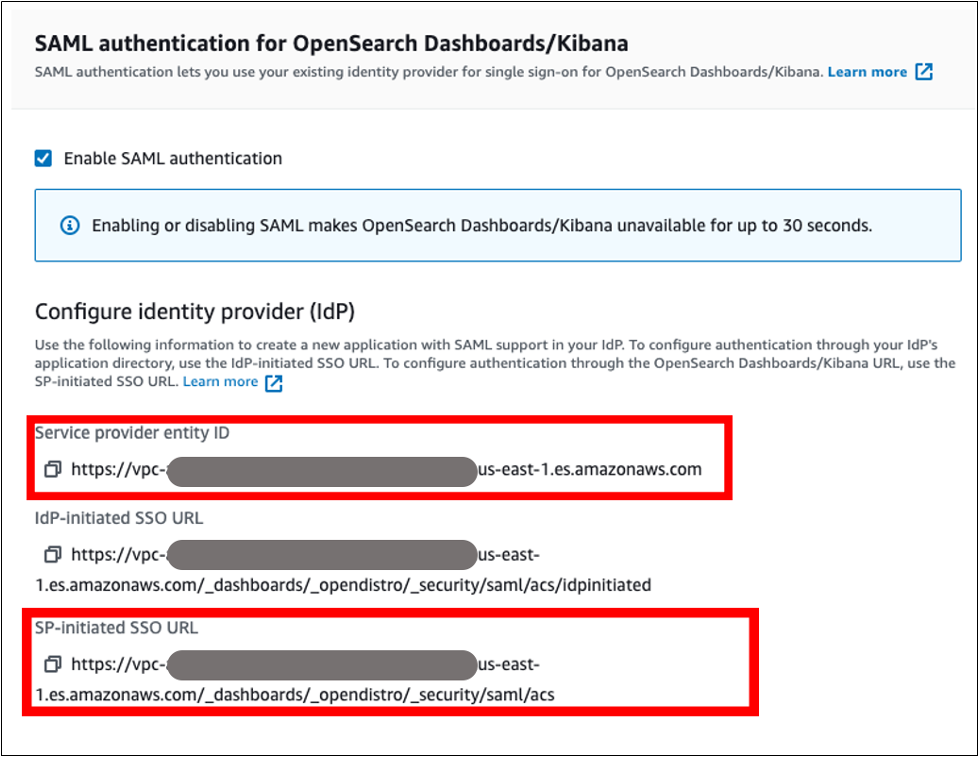\n\nFigure 8. Amazon OpenSearch Service URLs for SAML configuration\n\nWe will be using the **Service Provider entity ID** and **SP-initiated SSO URL** (highlighted in Figure 8) for Auth0 SAML configuration. We will complete the rest of the OpenSearch Service SAML configuration after the Auth0 SAML configuration.\n#### **Auth0 SAML configuration**\nGo back to Auth0.com, and navigate to **Applications** from the left menu. Then select the opensearch application that you created as a part of the Auth0 setup.\n- Click on the Addons tab on the application opensearch.\n- Click on the SAML2 WEB APP, then select Settings to provide SAML URLs from OpenSearch Service, as shown in Figure 9:\n \t- Application Callback URL = https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_dashboards/_opendistro/_security/saml/acs (SP-initiated SSO URL)\n\t- audience”: “https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com” (Service provider entity ID)\n\t- destination”: “ https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_plugin/kibana/_opendistro/_security/saml/acs” (SP-initiated SSO URL)\n\t- Mappings and other configurations shown in Figure 9\n```\n{\n \"audience\": \"https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com\",\n \"destination\": \"https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_plugin/kibana/_opendistro/_security/saml/acs\",\n \"mappings\":\n {\n \"email\":\n \"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress\",\n \"name\": \"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name\",\n \"groups\": \"http://schemas.xmlsoap.org/claims/Group\"\n },\n \"createUpnClaim\": false,\n \"passthroughClaimsWithNoMapping\": false,\n \"mapUnknownClaimsAsIs\": false,\n \"mapIdentities\": false,\n \"nameIdentifierFormat\":\n \"urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress\", \"nameIdentifierProbes\": [\n\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress\" ]\n}\n```\n\n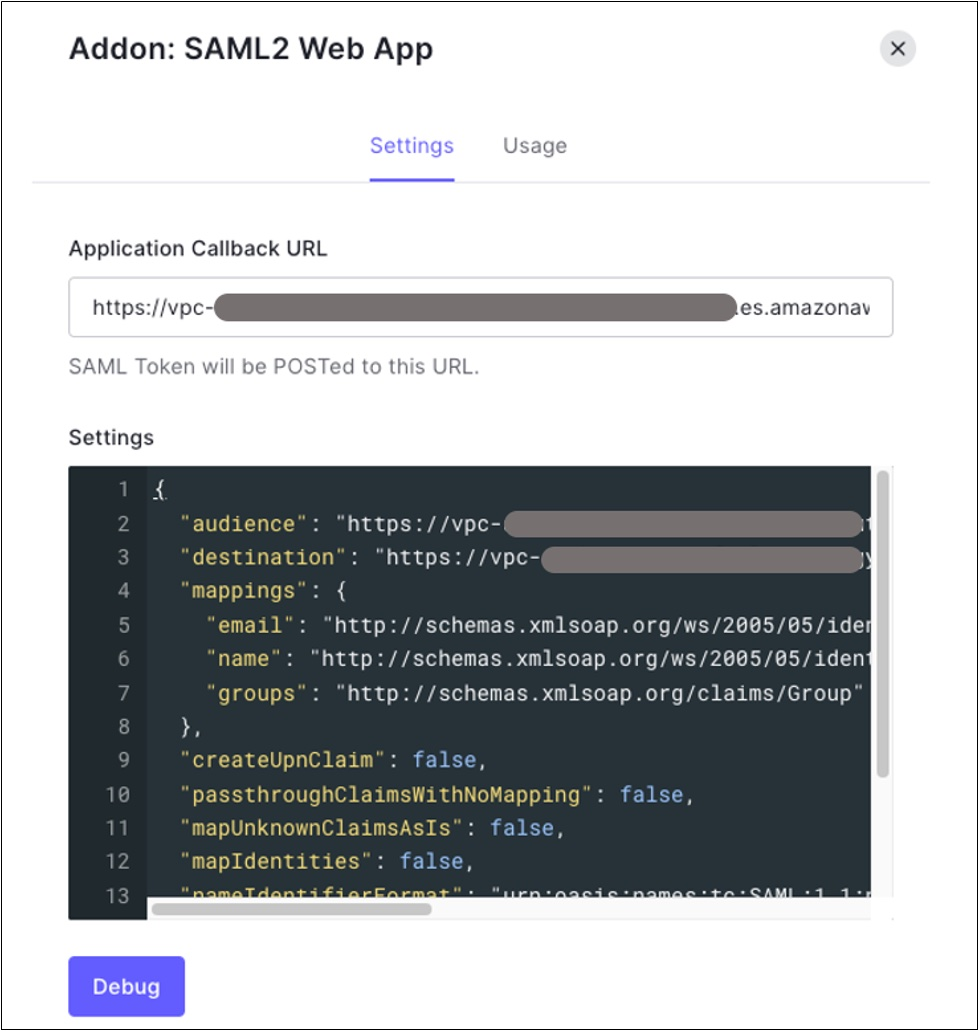\n\nFigure 9. Configuring Auth0 SAML parameters\n\n- Click on **Enable** to save the SAML configurations.\n- Go to the **Usage tab**, and click on the **Download** button to download Identity Provider Metadata, see Figure 10.\n\n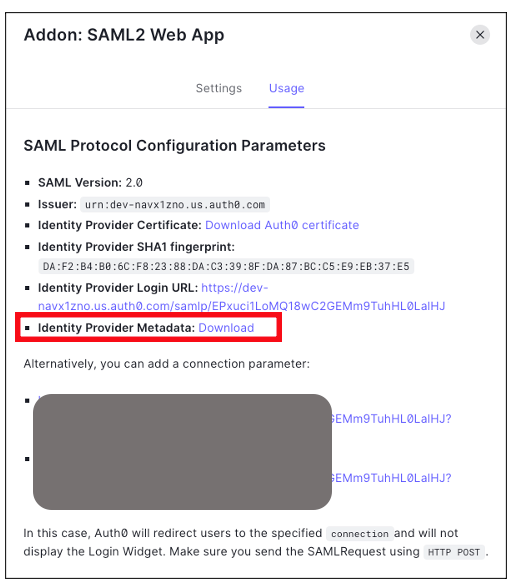\n\nFigure 10. Downloading Auth0 identity provider metadata for SAML configuration\n#### **OpenSearch Service SAML configuration**\n- Switch back to[ OpenSearch Service](https://console.aws.amazon.com/esv3/) domain:\n\t- Navigate to OpenSearch Service console\n\t- Click on **Actions**, then click on **Modify Security configuration**\n\t- Select Enable SAML authentication check box\n- Under **Import IdP metadata** section (Figure 11):\n\t- **Metadata from IdP**: Import the Auth0 identity provider metadata from downloaded XML file\n\t- **SAML master backend role: opensearch** (Auth0 group). Provide a SAML backend role/group SAML assertion key for group SSO into Kibana\n\t\n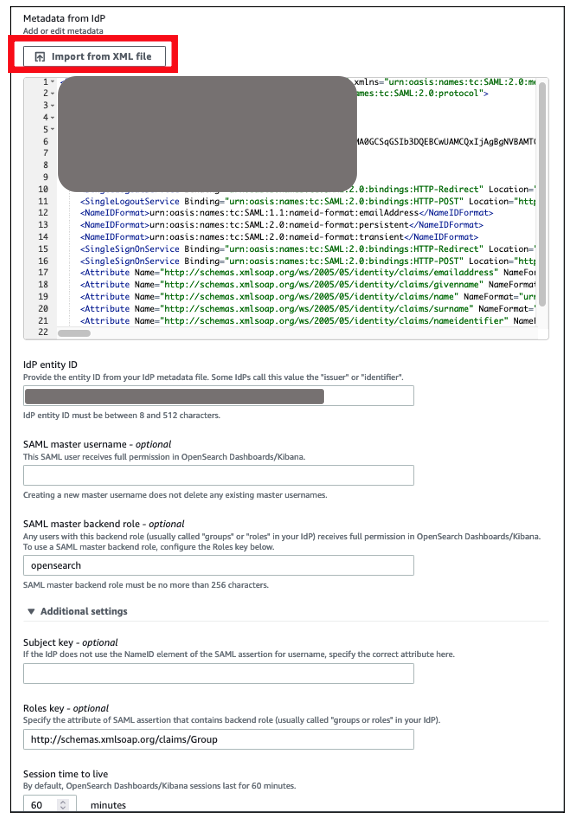\n\nFigure 11. Configuring Amazon OpenSearch Service SAML parameters\n\n- **Under Optional SAML settings** (Figure 12):\n\t- Leave **Subject Key** as blank, as Auth0 provides NameIdentifier\n\t- **Role key **should be **http://schemas.xmlsoap.org/claims/Group**. Auth0 lets you view a sample assertion during the configuration process by clicking on the **DEBUG** button on SAML2 WebApp. Tools like [ SAML-tracer](https://addons.mozilla.org/en-US/firefox/addon/saml-tracer/) can help you examine and troubleshoot the contents of real assertions.\n\t- **Session time to live (mins)**: 60\n\t\n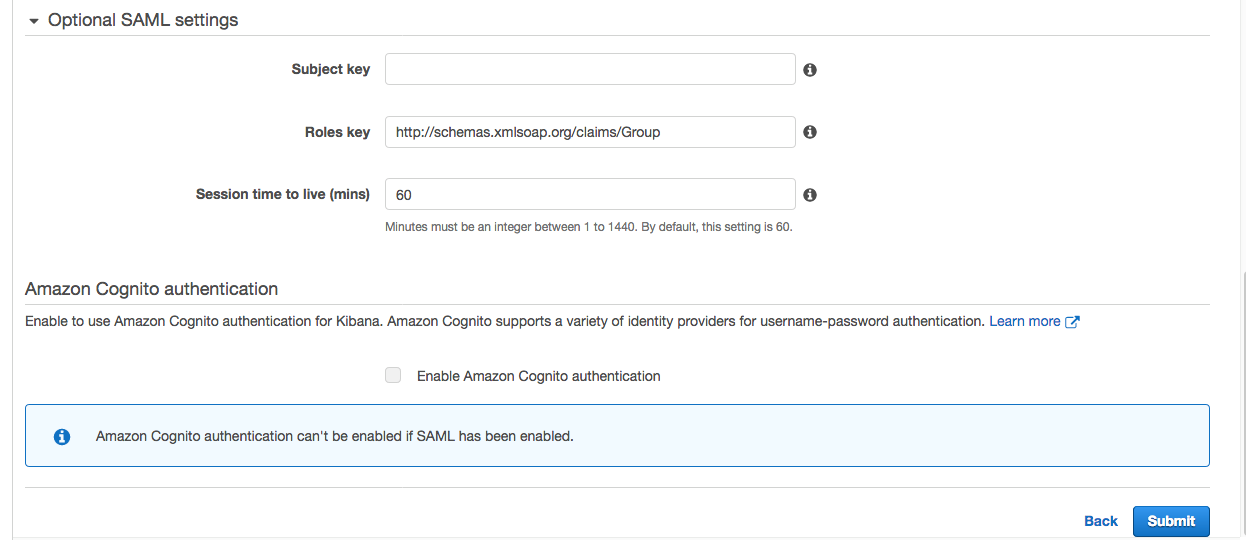\n\nFigure 12. Configuring Amazon OpenSearch Service optional SAML parameters\n\nClick on the **Save changes** button to complete OpenSearch Service SAML configuration for Kibana. We have successfully completed SAML configuration and are now ready for testing.\n#### **Validating access with Auth0 users**\n- Access OpenSearch Dashboards from the previously created OpenSearch Service cluster. The OpenSearch Dashboards URL can be found as shown in Figure 13. The first access to the OpenSearch Dashboards URL redirects you to the Auth0 login screen.\n 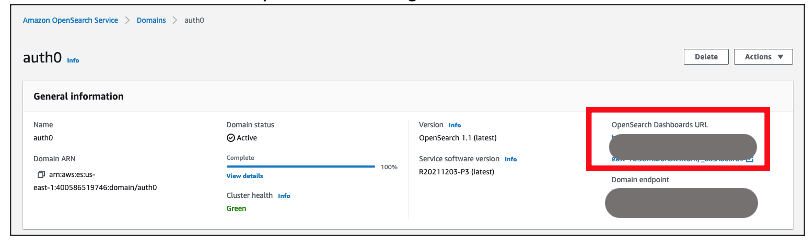\n\nFigure 13. Validating Auth0 users access with Amazon OpenSearch Service\n\n- Now copy and paste the OpenSearch Dashboards URL in your browser, and enter the user credentials.\n- If your OpenSearch Service domain is hosted within a private VPC, you will not be able to access your OpenSearch Dashboard over the public internet. But you can still use SAML as long as your browser can communicate with both your OpenSearch Service cluster and your identity provider.\n- You can create a Mac or Windows EC2 instance within the same VPC. This way you can access OpenSearch Dashboards from your EC2 instance’s web browser to validate your SAML configuration. You can also access OpenSearch Dashboards through Site-to-Site VPN from an on-premises environment.\n- After successful login, you will be redirected into the OpenSearch Dashboards home page. Explore our sample data and visualizations in OpenSearch Dashboards, as shown in Figure 14.\n\n\n\nFigure 14. SAML authenticated OpenSearch Dashboards\n\n- You now have successfully federated OpenSearch Dashboards with Auth0 as an identity provider. You can connect OpenSearch Dashboards by using your Auth0 credentials.\n\n#### **Cleaning up**\nAfter you test out this solution, remember to delete all the resources you created to avoid incurring future charges. Refer to these links:\n- [Deleting your OpenSearch Service domain](https://docs.aws.amazon.com/opensearch-service/latest/developerguide/gsgdeleting.html)\n- [Deleting your Auth0 account](https://community.auth0.com/t/remove-account-completely/11279)(if needed)\n#### **Conclusion**\nIn this blog post, we have demonstrated how to set up Auth0 as an identity provider over SAML authentication for OpenSearch Dashboards access. With this solution, you now have an OpenSearch Dashboard that uses Auth0 as the custom identity provider for your users. This reduces the customer login process to one set of credentials and improves employee productivity.\n\nGet started by checking the [Amazon OpenSearch Service Developer Guide](https://docs.aws.amazon.com/elasticsearch-service/latest/developerguide/what-is-amazon-elasticsearch-service.html), which provides guidance on how to build applications using OpenSearch Service for your operational analytics.\n\n\n\n**Raghavarao Sodabathina**\nRaghavarao Sodabathina is an Enterprise Solutions Architect at Amazon Web Services, focusing on Data Analytics, AI/ML, and Serverless Platform. He engages with customers to create innovative solutions that address customer business problems and to accelerate the adoption of Amazon Web Services services. In his spare time, Raghavarao enjoys spending time with his family, reading books, and watching movies.\n\n\n\n**Jana Gnanachandran**\nJana Gnanachandran is an Enterprise Solutions Architect at Amazon Web Services, focusing on Data Analytics, AI/ML, and Serverless platforms. He helps Amazon Web Services customers across numerous industries to design and build highly scalable, data-driven, analytical solutions to accelerate their cloud adoption. In his spare time, he enjoys playing tennis, 3D printing, and photography.","render":"<p><a href=\"https://aws.amazon.com/opensearch-service/\" target=\"_blank\">Amazon OpenSearch Service</a> is a fully managed, distributed, open search, and analytics service that is powered by the Apache Lucene search library. OpenSearch Service is derived from Elasticsearch 7.10.2, and is used for real-time application monitoring, log analytics, and website search. It’s ideal for use cases that require fast access and response for large volumes of data. OpenSearch Dashboards is derived from Kibana 7.10.2, and used for visual data exploration. With Security Assertion Markup Language (SAML)-based federation for OpenSearch Service, OpenSearch Dashboards lets you use your existing identity provider (IdP) like Auth0. You can use Auth0 to provide single sign-on (SSO) for OpenSearch Dashboards on OpenSearch Service domains. It also gives you fine-grained access control, and the ability to search your data and build visualizations. OpenSearch Service supports providers that use the SAML 2.0 standard, such as Auth0, Okta, Keycloak, Active Directory Federation Services (AD FS), and Ping Identity (PingID).</p>\n<p>In this post, we provide step-by-step guidance to show you how to set up a trial Auth0 account. We’ll demonstrate how to build users and groups within your organization’s directory, and enable SP-initiated single sign-on (SSO) into OpenSearch Dashboards.</p>\n<p>To use this feature, you must enable fine-grained access control. Rather than authenticating through <a href=\"https://aws.amazon.com/cognito/\" target=\"_blank\">Amazon Cognito</a> or an internal user database, SAML authentication for OpenSearch Dashboards lets you use third-party identity providers to log in to the OpenSearch Dashboards. SAML authentication for OpenSearch Dashboards is only for accessing the OpenSearch Dashboards through a web browser. Your SAML credentials do not let you make direct HTTP requests to OpenSearch Service or OpenSearch Dashboards APIs.</p>\n<p><a href=\"http://auth0.com/\" target=\"_blank\">Auth0</a> is an <a href=\"https://auth0.com/partners/aws\" target=\"_blank\">Amazon Web Services Competency Partner</a> and popular Identity-as-a-Service (IDaaS) solution. It supports both service provider (SP)-initiated and identity provider (IdP)-initiated SSO. For SP-initiated SSO, when you sign into the OpenSearch Dashboards login page it sends an authorization request to Auth0. Once it authenticates your identity, you are redirected to OpenSearch Dashboards. In IdP-initiated SSO, you log in to the Auth0 SSO page, and choose OpenSearch Dashboards to open the application.</p>\n<h4><a id=\"Overview_of_AuthO_SAML_authenticated_solution_7\"></a><strong>Overview of AuthO SAML authenticated solution</strong></h4>\n<p>Figure 1 depicts a sample architecture of a generic, integrated solution between Auth0 and OpenSearch Dashboards over SAML authentication.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/35b1677e662e42389cd7aaef9708bae3_image.png\" alt=\"image.png\" /></p>\n<p>Figure 1. A high-level view of a SAML transaction between Amazon OpenSearch Service and Auth0</p>\n<p>The sign-in flow is as follows:</p>\n<ol>\n<li>User opens browser window and navigates to OpenSearch Dashboards</li>\n<li>OpenSearch Service generates SAML authentication request</li>\n<li>OpenSearch Service redirects request back to browser</li>\n<li>Browser redirects to Auth0 URL</li>\n<li>Auth0 parses SAML request, authenticates user, and generates SAML response</li>\n<li>Auth0 returns encoded SAML response to browser</li>\n<li>Browser sends SAML response back to OpenSearch Service Assertion Consumer Service (ACS) URL</li>\n<li>ACS verifies SAML response</li>\n<li>User logs into OpenSearch Service domain</li>\n</ol>\n<h4><a id=\"Prerequisites_25\"></a><strong>Prerequisites</strong></h4>\n<p>For this walkthrough, you should have the following prerequisites:</p>\n<ol>\n<li>An <a href=\"https://signin.aws.amazon.com/signin?redirect_uri=https%3A%2F%2Fportal.aws.amazon.com%2Fbilling%2Fsignup%2Fresume&client_id=signup\" target=\"_blank\">Amazon Web Services account</a></li>\n<li>A virtual private cloud (VPC) based OpenSearch Service domain with fine-grained access control enabled</li>\n<li>An Auth0 account with user and a group</li>\n<li>A browser with network connectivity to Auth0, OpenSearch Service domain, and OpenSearch Dashboards</li>\n</ol>\n<p>The steps in this post are structured into the following sections:</p>\n<ol>\n<li>Identity provider (Auth0) setup</li>\n<li>Prepare OpenSearch Service for SAML configuration</li>\n<li>Identity provider (Auth0) SAML configuration</li>\n<li>Finish OpenSearch Service for SAML configuration</li>\n<li>Validation</li>\n<li>Cleanup</li>\n</ol>\n<h4><a id=\"Identity_provider_Auth0_setup_39\"></a><strong>Identity provider (Auth0) setup</strong></h4>\n<p><strong>Step 1: Sign up for an Auth0 account</strong></p>\n<ul>\n<li>Sign up for an <a href=\"https://auth0.com/signup\" target=\"_blank\"> Auth0 account</a>, then click on the <strong>Sign up</strong> button to complete your account setup.</li>\n<li>If you already have an account with Auth0, <a href=\"https://auth0.com/docs/authenticate/login\" target=\"_blank\">log in</a> to your Auth0 account.</li>\n</ul>\n<p><strong>Step 2: Create Groups in Auth0</strong></p>\n<ul>\n<li>Choose <strong>User Management</strong> in the left menu and click <strong>Users</strong>, then click on the <strong>+Create User</strong> button.</li>\n<li>Provide an email, password, and connection to your users. Click on the <strong>Create</strong> button to create your user.</li>\n<li>Add more users to your Auth0 account.</li>\n</ul>\n<p><strong>Step 3: Install Auth0 Extension to create a group and assign users to the group</strong></p>\n<ul>\n<li>Click on Extensions in the left menu and search for “<strong>Auth0 Authorization</strong>”. Click on <strong>Auth0 Authorization</strong> to install the extension, shown in Figure 2.</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/b4bd446df4534bfb9e3b801fbfb36950_image.png\" alt=\"image.png\" /></p>\n<p>Figure 2. Installing Auth0 Authorization extension</p>\n<ul>\n<li>Use all default options and click on the <strong>Install</strong> button to install the extension.</li>\n<li>Click on the <strong>Auth0 Authorization</strong> extension and choose the <strong>Accept</strong> button to provide access to your Auth0 account.</li>\n<li>The <strong>Auth0 Authorization</strong> extension must be configured. Click on <strong>Go to Configuration</strong> (Figure 3).<br />\n<img src=\"https://dev-media.amazoncloud.cn/e1e31ce790cb4718b6718127427861d1_image.png\" alt=\"image.png\" /></li>\n</ul>\n<p>Figure 3. Configuring the Auth0 Authorization extension</p>\n<ul>\n<li>Rotate your API keys and check Groups, Roles, and Permissions to provide authorization to the extension and then click on PUBLISH RULE to complete the configuration, see Figure 4.</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/e20daff76cab477cb03fbc2036be7dd9_image.png\" alt=\"image.png\" /></p>\n<p>Figure 4. Providing the permissions to Auth0 Authorization extension</p>\n<p><strong>Step 4: Create a group in Auth0</strong></p>\n<ul>\n<li>Choose <strong>Groups</strong> from the left menu and click on the <strong>Create your first Group</strong> button. For this example, we will create a group called opensearch for OpenSearch Dashboards access.</li>\n<li>Add your users to opensearch by clicking on <strong>ADD MEMBERS BUTTON</strong>, then click on the <strong>CONFIRM</strong> button to complete your group assignment (Figure 5).</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/5eaf947248674e51a0dec6c6580a0cb5_image.png\" alt=\"image.png\" /></p>\n<p>Figure 5. Adding users to Auth0 Group</p>\n<p><strong>Step 5: Create an Auth0 Application</strong></p>\n<p>Choose <strong>Applications</strong> from the left menu. Click on the <strong>+Create Application</strong> button.<br />\nFor this example, we are creating an application called “opensearch”.<br />\nSelect Single Page Web Applications, then click on the <strong>CREATE</strong> button to proceed.<br />\nClick on the <strong>Addons</strong> tab on the application Kibana (Figure 6).</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/2f8a563c25cb4289b5125149ea469ef4_image.png\" alt=\"image.png\" /></p>\n<p>Figure 6. Creating an Auth0 SAML application</p>\n<ul>\n<li>Click on the SAML2 WEB APP, then select settings to provide SAML URLs from OpenSearch Service. We will configure these details after preparing the OpenSearch Service cluster for SAML.</li>\n</ul>\n<h4><a id=\"Prepare_OpenSearch_Service_for_SAML_configuration_89\"></a><strong>Prepare OpenSearch Service for SAML configuration</strong></h4>\n<p>Once the OpenSearch Service domain is up and running, we can proceed with configuration.</p>\n<ul>\n<li>Under Actions, choose Edit security configuration (Figure 7).</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/14418bb1d55a4273aeec2db0ae0f4e5f_image.png\" alt=\"image.png\" /></p>\n<p>Figure 7. Enabling Amazon OpenSearch Service security configuration for SAML</p>\n<ul>\n<li>Under SAML authentication for OpenSearch Dashboards/Kibana, select the <strong>Enable SAML</strong> authentication check box (Figure 8). When we enable SAML, it will create different URLs required for configuring SAML with your identity provider.</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/87e6098afbbb4a32a608aa48a5a9e4f9_image.png\" alt=\"image.png\" /></p>\n<p>Figure 8. Amazon OpenSearch Service URLs for SAML configuration</p>\n<p>We will be using the <strong>Service Provider entity ID</strong> and <strong>SP-initiated SSO URL</strong> (highlighted in Figure 8) for Auth0 SAML configuration. We will complete the rest of the OpenSearch Service SAML configuration after the Auth0 SAML configuration.</p>\n<h4><a id=\"Auth0_SAML_configuration_105\"></a><strong>Auth0 SAML configuration</strong></h4>\n<p>Go back to Auth0.com, and navigate to <strong>Applications</strong> from the left menu. Then select the opensearch application that you created as a part of the Auth0 setup.</p>\n<ul>\n<li>Click on the Addons tab on the application opensearch.</li>\n<li>Click on the SAML2 WEB APP, then select Settings to provide SAML URLs from OpenSearch Service, as shown in Figure 9:\n<ul>\n<li>Application Callback URL = https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_dashboards/_opendistro/_security/saml/acs (SP-initiated SSO URL)</li>\n<li>audience”: “https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com” (Service provider entity ID)</li>\n<li>destination”: “ https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_plugin/kibana/_opendistro/_security/saml/acs” (SP-initiated SSO URL)</li>\n<li>Mappings and other configurations shown in Figure 9</li>\n</ul>\n</li>\n</ul>\n<pre><code class=\"lang-\">{\n "audience": "https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com",\n "destination": "https://vpc-XXXXX-XXXXX.us-east-1.es.amazonaws.com/_plugin/kibana/_opendistro/_security/saml/acs",\n "mappings":\n {\n "email":\n "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",\n "name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name",\n "groups": "http://schemas.xmlsoap.org/claims/Group"\n },\n "createUpnClaim": false,\n "passthroughClaimsWithNoMapping": false,\n "mapUnknownClaimsAsIs": false,\n "mapIdentities": false,\n "nameIdentifierFormat":\n "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress", "nameIdentifierProbes": [\n"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" ]\n}\n</code></pre>\n<p><img src=\"https://dev-media.amazoncloud.cn/8473b3b5f29f4bb3b9ac1d3854048fae_image.png\" alt=\"image.png\" /></p>\n<p>Figure 9. Configuring Auth0 SAML parameters</p>\n<ul>\n<li>Click on <strong>Enable</strong> to save the SAML configurations.</li>\n<li>Go to the <strong>Usage tab</strong>, and click on the <strong>Download</strong> button to download Identity Provider Metadata, see Figure 10.</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/aeab42bdbe724d10bc1fe141dd5bf929_image.png\" alt=\"image.png\" /></p>\n<p>Figure 10. Downloading Auth0 identity provider metadata for SAML configuration</p>\n<h4><a id=\"OpenSearch_Service_SAML_configuration_144\"></a><strong>OpenSearch Service SAML configuration</strong></h4>\n<ul>\n<li>Switch back to<a href=\"https://console.aws.amazon.com/esv3/\" target=\"_blank\"> OpenSearch Service</a> domain:\n<ul>\n<li>Navigate to OpenSearch Service console</li>\n<li>Click on <strong>Actions</strong>, then click on <strong>Modify Security configuration</strong></li>\n<li>Select Enable SAML authentication check box</li>\n</ul>\n</li>\n<li>Under <strong>Import IdP metadata</strong> section (Figure 11):\n<ul>\n<li><strong>Metadata from IdP</strong>: Import the Auth0 identity provider metadata from downloaded XML file</li>\n<li><strong>SAML master backend role: opensearch</strong> (Auth0 group). Provide a SAML backend role/group SAML assertion key for group SSO into Kibana</li>\n</ul>\n</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/6a65ef41740c4591a5d0bc12961977b3_image.png\" alt=\"image.png\" /></p>\n<p>Figure 11. Configuring Amazon OpenSearch Service SAML parameters</p>\n<ul>\n<li><strong>Under Optional SAML settings</strong> (Figure 12):\n<ul>\n<li>Leave <strong>Subject Key</strong> as blank, as Auth0 provides NameIdentifier</li>\n<li>**Role key **should be <strong>http://schemas.xmlsoap.org/claims/Group</strong>. Auth0 lets you view a sample assertion during the configuration process by clicking on the <strong>DEBUG</strong> button on SAML2 WebApp. Tools like <a href=\"https://addons.mozilla.org/en-US/firefox/addon/saml-tracer/\" target=\"_blank\"> SAML-tracer</a> can help you examine and troubleshoot the contents of real assertions.</li>\n<li><strong>Session time to live (mins)</strong>: 60</li>\n</ul>\n</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/715b27df92f14488bbdd58e02c1741fc_image.png\" alt=\"image.png\" /></p>\n<p>Figure 12. Configuring Amazon OpenSearch Service optional SAML parameters</p>\n<p>Click on the <strong>Save changes</strong> button to complete OpenSearch Service SAML configuration for Kibana. We have successfully completed SAML configuration and are now ready for testing.</p>\n<h4><a id=\"Validating_access_with_Auth0_users_167\"></a><strong>Validating access with Auth0 users</strong></h4>\n<ul>\n<li>Access OpenSearch Dashboards from the previously created OpenSearch Service cluster. The OpenSearch Dashboards URL can be found as shown in Figure 13. The first access to the OpenSearch Dashboards URL redirects you to the Auth0 login screen.<br />\n<img src=\"https://dev-media.amazoncloud.cn/db2357b97c7a45b4aa2628f4044188ed_image.png\" alt=\"image.png\" /></li>\n</ul>\n<p>Figure 13. Validating Auth0 users access with Amazon OpenSearch Service</p>\n<ul>\n<li>Now copy and paste the OpenSearch Dashboards URL in your browser, and enter the user credentials.</li>\n<li>If your OpenSearch Service domain is hosted within a private VPC, you will not be able to access your OpenSearch Dashboard over the public internet. But you can still use SAML as long as your browser can communicate with both your OpenSearch Service cluster and your identity provider.</li>\n<li>You can create a Mac or Windows EC2 instance within the same VPC. This way you can access OpenSearch Dashboards from your EC2 instance’s web browser to validate your SAML configuration. You can also access OpenSearch Dashboards through Site-to-Site VPN from an on-premises environment.</li>\n<li>After successful login, you will be redirected into the OpenSearch Dashboards home page. Explore our sample data and visualizations in OpenSearch Dashboards, as shown in Figure 14.</li>\n</ul>\n<p><img src=\"https://dev-media.amazoncloud.cn/43632ce27a62499abf3c8044aa751a58_image.png\" alt=\"image.png\" /></p>\n<p>Figure 14. SAML authenticated OpenSearch Dashboards</p>\n<ul>\n<li>You now have successfully federated OpenSearch Dashboards with Auth0 as an identity provider. You can connect OpenSearch Dashboards by using your Auth0 credentials.</li>\n</ul>\n<h4><a id=\"Cleaning_up_184\"></a><strong>Cleaning up</strong></h4>\n<p>After you test out this solution, remember to delete all the resources you created to avoid incurring future charges. Refer to these links:</p>\n<ul>\n<li><a href=\"https://docs.aws.amazon.com/opensearch-service/latest/developerguide/gsgdeleting.html\" target=\"_blank\">Deleting your OpenSearch Service domain</a></li>\n<li><a href=\"https://community.auth0.com/t/remove-account-completely/11279\" target=\"_blank\">Deleting your Auth0 account</a>(if needed)</li>\n</ul>\n<h4><a id=\"Conclusion_188\"></a><strong>Conclusion</strong></h4>\n<p>In this blog post, we have demonstrated how to set up Auth0 as an identity provider over SAML authentication for OpenSearch Dashboards access. With this solution, you now have an OpenSearch Dashboard that uses Auth0 as the custom identity provider for your users. This reduces the customer login process to one set of credentials and improves employee productivity.</p>\n<p>Get started by checking the <a href=\"https://docs.aws.amazon.com/elasticsearch-service/latest/developerguide/what-is-amazon-elasticsearch-service.html\" target=\"_blank\">Amazon OpenSearch Service Developer Guide</a>, which provides guidance on how to build applications using OpenSearch Service for your operational analytics.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/e36c02027b704265834f915cfb72fa8c_image.png\" alt=\"image.png\" /></p>\n<p><strong>Raghavarao Sodabathina</strong><br />\nRaghavarao Sodabathina is an Enterprise Solutions Architect at Amazon Web Services, focusing on Data Analytics, AI/ML, and Serverless Platform. He engages with customers to create innovative solutions that address customer business problems and to accelerate the adoption of Amazon Web Services services. In his spare time, Raghavarao enjoys spending time with his family, reading books, and watching movies.</p>\n<p><img src=\"https://dev-media.amazoncloud.cn/5675cd73dcfb44f99f98a7d335388336_image.png\" alt=\"image.png\" /></p>\n<p><strong>Jana Gnanachandran</strong><br />\nJana Gnanachandran is an Enterprise Solutions Architect at Amazon Web Services, focusing on Data Analytics, AI/ML, and Serverless platforms. He helps Amazon Web Services customers across numerous industries to design and build highly scalable, data-driven, analytical solutions to accelerate their cloud adoption. In his spare time, he enjoys playing tennis, 3D printing, and photography.</p>\n"}
Building SAML federation for Amazon OpenSearch Service with Auth0
海外精选
海外精选的内容汇集了全球优质的亚马逊云科技相关技术内容。同时,内容中提到的“AWS”
是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。

 0
0 0
0亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
目录
亚马逊云科技解决方案 基于行业客户应用场景及技术领域的解决方案
联系亚马逊云科技专家
亚马逊云科技解决方案
基于行业客户应用场景及技术领域的解决方案
联系专家
0
目录
 分享
分享 点赞
点赞 收藏
收藏 目录
目录立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
立即关注

亚马逊云开发者
公众号

User Group
公众号

亚马逊云科技
官方小程序
“AWS” 是 “Amazon Web Services” 的缩写,在此网站不作为商标展示。
